THE ULTIMATE ONLINE PRIVACY GUIDE
https://darknetmarkets.org/guides/the-ultimate-online-privacy-guide/
Ladies and Gentlemen, here it is. We’ve put a lot of effort into this, and it’s very long. We tried to think of every angle in terms of privacy, and the effort was worth it. Almost 13,000 words about how to protect your privacy online. There’s no need to read it at once, just check the index below and click on the parts that interest you.
Update 08 May 2014: in addition to many minor updates, we have included a whole new section on the Heatbleed Bug, have completely revamped the section on Encryption to better reflect the ongoing revelations about the NSA’s concerted attempt to subvert all encryption standards (possibly with NIST help), and have noted the results of the first phase of the ongoing audit of TrueCrypt.
Update 17 June 2014: in a move that is as surprising as it is baffling, the devs behind TrueCrypt have pulled the plug on the popular full-disk encryption program. Conspiracy theories abound, and while some developers seek to fork the software, Phase II of the audit goes ahead. For more details on the story see here and here. Until the audit is complete, we strongly suggest avoiding TrueCrypt, and migrating TrueCrypt containers to other programs, such as to https://diskcryptor.net/wiki/Main_Page for Windows users, or https://code.google.com/p/cryptsetup/ and bwalex/tc-play (a free TrueCrypt Implementation based on dm-crypt) for Linux users.
Index
Introduction
So how secure is encryption?
Use Foss Software
Pay for stuff anonymously
Anonymise your internet use
Secure your browsing
Secure your email
Use antivirus, anti-malware and firewall software
Miscellaneous security hints and tips and tricks
http://www.guardian.co.uk/world/interactive/2013/jun/20/exhibit-b-nsa-procedures-document, but what it boils down to is that data from US citizens is examined, and then discarded if found to be uninteresting to the NSA. Encrypted data on the other hand is stored indefinitely, until such time as the NSA can decrypt it. All data relating to non-US citizens can be kept indefinitely, but sheer practicality suggests that encrypted data gets special attention.
If a lot more people start to use encryption, then encrypted data will stand out less, and surveillance organizations’ job of invading everyone’s privacy will be made much lot harder. Remember – anonymity is not a crime!
scale of the NSA’s deliberate assault on global encryption standards and the on-going fiasco that is the Heartbleed Bug, confidence in encryption is not as high as it was just a few months ago, so let’s examine the current state of play…
require 3.4 x10(38) operations to reliably break
It should be noted that the US government uses 256-bit encryption to protect ‘sensitive’ data (and 128-bit for ‘routine’ encryption needs). However the method it uses is AES, which as we shall discuss below is not without problems.
Heartbleed Bug.
NIST
works closely with the NSA in the development of its cyphers. Given what we now know of the NSA’s systematic efforts to weaken or built back doors into international encryption standards, there is every reason to question the integrity of NIST algorithms.
Although NIST has been quick to deny any wrong doing (‘NIST would not deliberately weaken a cryptographic standard’), and has invited public participation in a number of http://csrc.nist.gov/publications/PubsDrafts.htmlin a move designed to bolster public confidence, the New York Times has accused the NSA of circumventing the NIST approved encryption standards by either introducing undetectable backdoors, or subverting the public development process to weaken the algorithms.
Any existing trust was pretty much destroyed by news that a NIST certified cryptographic standard – the Dual Elliptic Curve algorithm (Dual_EC_DRGB) had been deliberately weakened not just once, but twice, by the NSA.
That there might be deliberate backdoor in Dual_EC_DRGB had already been noticed before. In 2006 researchers at the Eindhoven University of Technology in the Netherlands noted that an attack against it was easy enough to launch on ‘an ordinary PC’, and Microsoft engineers flagging up a suspected backdoor in the algorithm. Despite these concerns however, where NIST leads, industry follows, and Microsoft, Cisco, Symantec and RSA all http://csrc.nist.gov/groups/STM/cavp/documents/drbg/drbgval.html, in large part due the fact that compliance with NIST standards is a prerequisite to obtaining US government contracts.
When you consider that NIST certified cryptographic standards are pretty much ubiquitous worldwide throughout all areas of industry and business that rely on privacy (including the VPN industry), this is all rather chilling. Perhaps precisely because so much relies on these standards, cryptography experts have been unwilling to face up to the problem – at least until Silent Circle, the company which closed its Silent Mail service rather than see it compromised by the NSA, announced in November 2013 that it planned to https://www.bestvpn.com/blog/7703/silent-circle-moves-away-nist-encryption-standards/.
NSA attacks on RSA key encryption
revelations that came out of the new information provided by Edward Snowden in September is that, “another program, codenamed Cheesy Name, was aimed at singling out encryption keys, known as ‘certificates’, that might be vulnerable to being cracked by GCHQ supercomputers.”
That these certificates can be ‘singled out’ strongly suggests that 1024-bit RSA encryption (commonly used to protect the certificate keys) is weaker than previously thought, and can be decrypted much more quickly than expected by the NSA and GHCQ. Once a certificate key has been decrypted, then all exchanges past and future will be compromised if non ephemeral key exchange is used (i.e. if, as is depressingly common practice, a single permanent private key is used to decrypt all data).
This means that many forms of encryption which rely on certificates and non ephemeral keys must be regarded broken, including SSL and TLS. This has huge implications for all HTTPS traffic.
The good news is that OpenVPN, which uses ephemeral (temporary) key exchanges, should not be affected. This is because with ephemeral key exchanges a new key is generated for each exchange, and there is therefore no reliance on certificates to establish trust. Even if an adversary were to obtain the private key of a certificate, they could not decrypt the communication. It is possible that a man in the middle (MitM) attack could target an OpenVPN connection if the private key has been comprised, but this would have to be specifically targeted attack. Unfortunately, OpenVPN uses the OpenSSL library, and may be vulnerable to Heartbleed.
Since news that the NSA (and GHCQ) can crack 1028-bit RSA encryption became public, some VPN providers at least have beefed up their key encryption to 2048-bits, or even up to 4096-bits.
Perfect Forward Secrecy
perfect forward secrecy, a system whereby a new and unique (with no additional keys derived from it) private encryption key is generated for each session. (i.e. use of ephemeral key exchanges).
Although still in the minority, more companies are beginning to use ephemeral keys, and those which do are largely immune to the Heartbleed Bug.
The takeaway – or So is encryption secure?
It is becoming abundantly clear that to underestimate the NSA’s ambition or ability compromise all encryption is a bad mistake. However, it remains the best defence we have against them (and others like them), and to the best of anyone’s knowledge strong ciphers such as AES (despite out misgivings about its NIST certification) and OpenVPN (once patched against the Heartbleed bug) remain secure.
As Bruce Schneier, encryption specialist, fellow at Harvard’s Berkman Center for Internet and Society and privacy advocate says,
‘Trust the math. Encryption is your friend. Use it well, and do your best to ensure that nothing can compromise it. That’s how you can remain secure even in the face of the NSA.’
It is also worth remembering that the NSA is not the only potential adversary, and most criminals and even government organisations have nowhere near as much ability to circumvent encryption as the NSA does.
The importance of end-to-end encryption
inspection by the NSA.
Basically, services that encrypt your data on their servers, rather than you encrypting your own data on your own machine, should be strongly avoided.
Metadata
powerful tool in the wrong hands (i.e. just about anybody).
For example, even if using a securely encrypted end-to-end voice service such as Silent Circle, your ISP (and anyone else watching) will still be able to tell who you are making the call to, whether you are calling from your usual location, how often you call, how long you usually chat, and much more. With such information it would be trivially easy to discover that you were having an affair (for example)…
However, the reason we said ‘not necessarily protect users’ is that technologies such as VPN and Tor do make the collection of metadata very difficult. In the example above, if you always connected to a VPN service when using the internet, all a watcher could tell is that you are connected to a VPN server, not that that you are using Silent Circle, let alone where and when you are using it…
Although the NSA does target individual communications, its primary concern is the collection of metadata.
https://www.bestvpn.com/blog/9430/did-the-nsa-know-about-the-heartbleed-bug/ in the open source code of OpenSSL versions 1.01 through 1.0.1f (inclusive), represents perhaps the most ‘catastrophic’ threat to online security yet.
OpenSSL is by far the most commonly used cryptographic library on the internet, used by banks, VPN companies, online storage services – basically almost everything that requires a secure internet connection, and it is estimated that over two thirds of the internet was affected by the bug which went unnoticed by the cryptographic community for almost a year and half.
Even worse, if a system has been compromised using the Bug there is no way to know about it, and given the huge amounts of resources the NSA has at its disposal to discover such cryptographic weaknesses, it is likely that it, at the very least, https://www.bestvpn.com/blog/9430/did-the-nsa-know-about-the-heartbleed-bug/ about the bug but didn’t bother to tell anyone.
By exploiting the bug an attacker can access users’ accounts, steal their passwords, and even https://www.bestvpn.com/blog/9445/heartbleed-can-be-used-to-steal-ssl-keys/. Yup, disastrous is the word! Hopefully most websites and services using the vulnerable versions of OpenSSL (ones using older versions were not affected) have updated their OpenSSL libraries to patch the vulnerability, plus re-issued their SSL certificates as these may have been compromised. Unfortunately this may be a somewhat forlorn hope, as at the time of writing almost half of the servers believed to be vulnerable in the days immediately following the Heartbleed disclosure remain susceptible.
Being sure that companies have done this is difficult however, and so far . A number of online tools are available to test servers for vulnerability to Heartbleed, but as this report details, these may not be completely reliable.
The whole mess is compounded by the fact that many companies claim to have fixed the problem simply because they have patched the vulnerability, but have not changed their SSL certificates. This is a bit like putting a fancy padlock on a glass door, as if they have already been compromised and the attacker already has access to the SSL certificates, they will still have full access the server.
If you are unsure about whether a particular service has properly fixed the problem, the best thing you can probably do is to contact them and ask what the situation is.
Most of the fixing is a server-side issue, and there is nothing you can do as a user, but once fixed it is essential that you change your passwords immediately! If a server has been compromised at any time over the last year and half the attacker will have your password, and if you use that password on more than one site, they can use it to compromise even services that were unaffected by the Heartbleed Bug.
What this means is that by now you should change your all your passwords (although if you change your password before a site has completely fixed all Heartbleed issues then it is still potentially vulnerable to hackers).
See our section in this Guide on how to make your passwords more secure. Ideally you should use a different password for every service and website you use (at least the important ones), so a password manager program may be the best solution.
One final note is that websites which have had the foresight to to implement Perfect Forward Secrecy are largely unaffected by the Heartbleed Bug, even if using a compromised version of OpenSSL.
no proprietary software can be trusted; even software specifically designed with security in mind. It is now a proven fact that the NSA has co-opted or coerced hundreds of technology companies into building backdoors into their programs, or otherwise weakening security in order to allow the NSA access. US and UK companies are particularly suspect, although the reports make it clear that company’s across the world have acceded to NSA demands.
The problem with proprietary software is not just that as sole developers and owners, companies can be fairly easily approached and convinced to play ball with the NSA, but that their source code is kept secret, making it easy to add to or modify in dodgy ways without anyone noticing.
The best answer to this problem is to use free open source software (FOSS). Often jointly developed by disparate and otherwise unconnected individuals, the source code is available to everyone to examine and peer-review, thereby minimizing the chances that it has been tampered with. Ideally this code should also be compatible other implementations, in order to minimize the possibility of a back-door being built in.
It is of course possible that NSA agents have infiltrated open source development groups and introduced malicious code without anyone’s knowledge, and the sheer amount of code that many projects involve means that it is often almost impossible to fully peer-review all of it. Still, despite these potential pitfalls, FOSS remains the most reliable and least likely to be tampered with software available, and if you truly care about privacy you should try to use it exclusively (up to and including using FOSS Operating Systems such as Linux).
Mullvad, will even take cash sent anonymously in the post.
5 Best VPNs that accept Bitcoin!) that aim to improve users’ anonymity,
One important thing to understand is that Bitcoin is not inherently anonymous. The exciting thing is that with care it can be made so.
Buying Bitcoins Anonymously
Most Bitcoin traders are located in the US and have US based bank accounts, which can make buying Bitcoins outside the States both a little involved, and location dependent. However, the following methods are common ways to obtain Bitcoins anonymously.
For maximum anonymity:
Neither the cheapest nor the most anonymous method, this is the most convenient, and does nevertheless ensure a high degree of anonymity. Using this method you do not actually buy your Bitcoins anonymously; you simply purchase them from an automated Bitcoin exchange (such as CoinBase), and then ‘launder’ them using a ‘mixer’ service such as Blockchain.info Shared Send.
A mixer service basically anonymises your Bitcoins by swapping them with multiple other users, making it very difficult (but not impossible for a determined investigator) to follow the chain back to you. Services such as this are, of course, not free (Blockchain.info for example charges a 0.5% fee).
Many automatic exchanges require you to prove your real world identity, in which case it is easy to determine that you have purchased Bitcoins (but not what happens to them after that if you mix them).
2. Use pre-paid credit cards
This method is somewhat location dependent, but in most areas it is possible to buy pre-paid ‘gift’ credit cards over-the-counter, which can then be used to buy Bitcoins anonymously if the transaction is performed through disposable email addresses etc. Alternatively, you can just use the card to buy an on-line service directly!
3. Buy locally with cash
The website LocalBitcoins.com lets you find Bitcoin sellers who live near you. Once you have found a seller you are happy with, it is up to you to contact them and to arrange a meeting.
Prices are generally higher than those on Mt Gox, and you should pay attention to the feedback to ensure the seller is highly scored (it works much like the feedback system on eBay).
4. Buy from an individual seller online
This can be done on LocalBitcoins.com, or in the #bitcoin-otc chatroom on Freenode (otc = over-the -counter).
#bitcoin-otc uses a quite involved feedback system, which it is well worth spending the time to understand, and you will need to hash out the payment method with the seller. A list of IRC client can be found here.
here, and some of the pros and cons of the ‘top 5’ are outlined in this article.
We have written an extensive guide to buying and paying for VPN (although the same principles apply to any service of course) anonymously using Bitcoins, starting here.
this article, but to summarize…
Mullvad, AirVPN and Private Internet Access (although the fact that PIA is US based has introduced considerable uncertainty to this recommendation).
Pros:
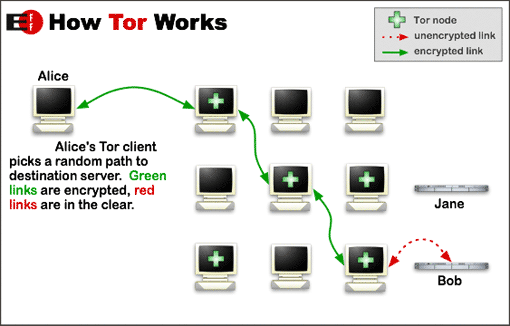
The final link in the chain, the one that connects you to the internet, is known as an exit node, and is one of the biggest weaknesses of the system. Nodes are run by volunteers, and those running exit nodes are vulnerable to prosecution over the behaviour of other Tor users who have used the system for illegal purposes (including piracy and much worse), as the IP of the offenders can been traced to the exit node’s IP address.
This has led to a fairly small number of public exit nodes being available, and has meant that restrictive governments such as China, who monitor these nodes, have been able to block access to many of them. There are still plenty of nodes around however, but it does mean that Tor users in some countries my need to reconnect to a number of different nodes before they find one that has not been blocked.
The other big problem with Tor is that it is very slow, as users’ data is routed through a number of servers randomly located anywhere in the world before connecting to the internet.
Pros:
For the really paranoid out there, it is possible to route a VPN connection through Tor, or an OpenVPN connection through an SSL or SSH tunnel (in order to hide its use). More details about these methods can be found here.
A final note regarding Tor is that it makes the anarchic and entirely unregulated Silk Road style marketplaces possible (such as Silk Road 2.0), as the online black market exists entirely within the Tor network (and therefore has no need for vulnerable exit nodes). Although supposedly set up on libertarian ideals, much of the actively on these marketplaces is highly illegal, so if you are curious then you will have to investigate further on your own.
in our opinion they are inferior to VPN.
Other services which may be of interest include JonDonym, http://www.bestvpn.com/blog/6507/lahana-service-aims-to-circumvent-censorship-in-turkey/, I2P and Psiphon. Interestingly, many such services can be combined with Tor and/or VPN for greater security.
cookies, how to clear them, and that most browsers now have aPrivate Browsing mode that not only prevents the browser from saving your internet history, but also blocks these cookies. It is therefore a good idea to always surf using Private Browsing, but this alone is not enough to stop you being tracked across the internet, as your browser leaves many other traces as it goes…
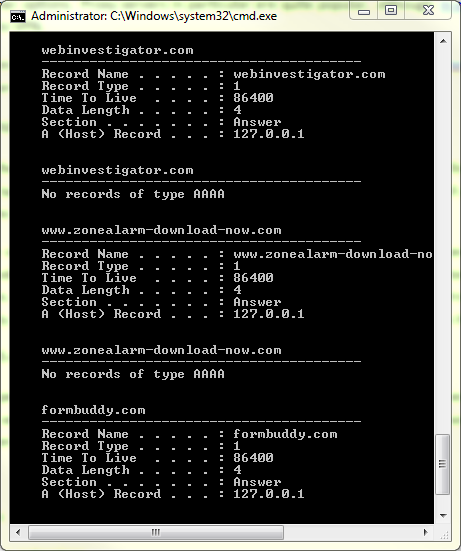
In Windows you can see what DNS information has been cached by typing ‘ipconfig /displaydns’ at the command prompt (cmd.exe)
Thanks to growing awareness of Flash cookies, including the so-called ‘zombie cookies’ (bits of persistent Flash code which respawn regular cookies when they are modified or deleted), and the fact that most modern browsers include Flash cookies as part of their regular cookie control features, the use of Flash cookies is declining (although they still represent a serious threat).
We have a detailed article on Flash cookies, the dangers they pose, and how to prevent them available here.
this article.
Interestingly, the recently released Privacy Badger browser plugin from the Electronic Frontier Foundation promises that it will add protection against fingerprinting, although how this will work we have no idea. Once it has been implemented and we have had a chance to test it out, we will update this section.
HTML web storage – built into HTML5 (the much vaunted replacement to Flash) is Web storage (also known as DOM (Document Object Model) storage). Even creepier and much more powerful than cookies, web storage is a way analogous to cookies of storing data in a web browser, but which is much more persistent, has a much greater storage capacity, and which cannot normally be monitored, read, or selectively removed from your web browser.
Web storage is enabled in all browsers by default, but in Firefox and Internet Explorer it can be turned off. Firefox users can also configure the https://addons.mozilla.org/en-US/firefox/addon/betterprivacy/addon to remove web storage automatically on a regular basis, or you can use the https://addons.mozilla.org/en-US/firefox/addon/clickclean/ addon, while Chrome users can use the Click&Clean extension or, alternatively, the versatilehttps://chrome.google.com/extensions/detail/odjhifogjcknibkahlpidmdajjpkkcfn extension (but this requires a high degree of configuring). Remember that using these addons will increase you browser fingerprint uniqueness. More details, including instructions on how to web storage off in Firefox and IE are available in our article here.
ETags – part of HTTP, the protocol for the World Wide Web, Etags are markers used by your browser to track resource changes at specific URL. By comparing these changes in these markers with a database, websites can build up a fingerprint which can be used to track you. They can also be used to respawn (Zombie style) HTTP and HTML5 cookies, and once set on one site, used by associate companies to also track you.
Unfortunately this kind of cache tracking is virtually undetectable, so reliable prevention is very hard. Clearing your cache between each website you visit should work, as should turning off your cache altogether. Unfortunately these methods are arduous, and will negatively impact your browsing experience. The Firefox add-on Secret Agent prevents tracking by ETags, but, again, will likely increase your browser fingerprint (or because of the way it works, maybe not). For more details see here.
History stealing – Now we start to get really scary. History stealing (also known as history snooping) exploits the way in which the Web is designed, allowing a website you visit to discover your past browsing history. Seeour article for a fuller explanation of how it works, but the bad news is, a) this information can be combined with social network profiling to uniquely identify you and, b) it is almost impossible to prevent.
The only good news here is that social network fingerprinting, while scarily effective, is not reliable, and if you mask your IP address with a VPN (or Tor) then you will be going a long way towards disassociating your real identity from your tracked web behavior.
AdBlock Plus (Firefox, Chrome, Opera, Android) – this fantastic and must-have extension blocks all manner of adverts, even Facebook ads and those embedded within YouTube videos (here in the UK it even blocks 4oD ads!). In addition to this, it warns you when visiting known malware hosting websites, and disables third party tracking cookies and scripts. Unlike NoScript (see below), AdBlock Plus is very easy to use while still remaining powerful. By default, AdBlock Plus allows ‘some not intrusive advertising’. This can be turned off (Add-ons -> Extensions -> AdBock Plus -> Filter preferences), or you can install AdBlock Edge for Firefox, a fork of AdBlock Plus that removes this ‘feature’
Note that this list is not exhaustive of all the great privacy related browser extensions out there, and there are good articles about other extensions for Firefox and https://www.bestvpn.com/blog/9019/recommended-chrome-and-chromium-security-extensions/. We also have an article on how you make Firefox even more secure by changing setting in about:config.
Also, as noted above, you should be aware that using any browser plugin increases your browser uniqueness, which makes you more susceptible to being tracked by browser fingerprinting. Unfortunately there is little practical most of us can do about it (although the EFF promise to add Fingerprinting protection to Privacy Badger).
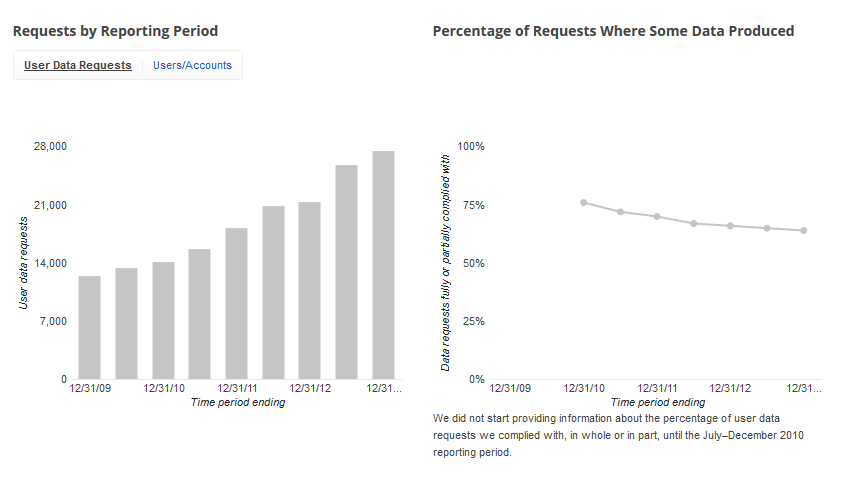
Google Transparency Report on the number of User Data Requests received, and the number (at least partially) acceded to.
There are however some search engines that do not collect user’s data. DuckDuckGo in particular has grabbed the headlines of late, with its popularity shooting through the roof following the NSA spying revelations (daily searches on DuckDuckGo jumped from the 2 million it had built up over the last four and a half years, to 3 million in just 8 days!).
An added benefit of using a search engine that does not track you is that it avoids the ‘filter bubble’. Most search engines use your past search terms (and things you ‘Like’ on social networks) to profile you, so they can return results they think will interest you. This can result in only receiving search returns that agree with your point of view, locking you into a ‘filter bubble’ where you do not get to see alternative viewpoints and opinions because they have been downgraded in your search results.
Not only does this deny you access to the rich texture and multiplicity of human input, but it can also be very dangerous as it can confirm prejudices and prevent you from seeing the ‘bigger picture’.
DuckDuckGo – the best known alternative search engine, and one we have examined in some detailhere, DuckDuckGo pledges not to track it users. Each search event is anonymous, and while it could in theory be tracked, there is no profile attached that can be accessed by infiltrators. DuckDuckGo says that it would comply with ordered legal requests, but as it doesn’t track users, ‘there is nothing useful to give them’. In use we have found DuckDuckGo to be very good, and through the use of ‘bangs’, it can also be made to search most other popular search engines anonymously too
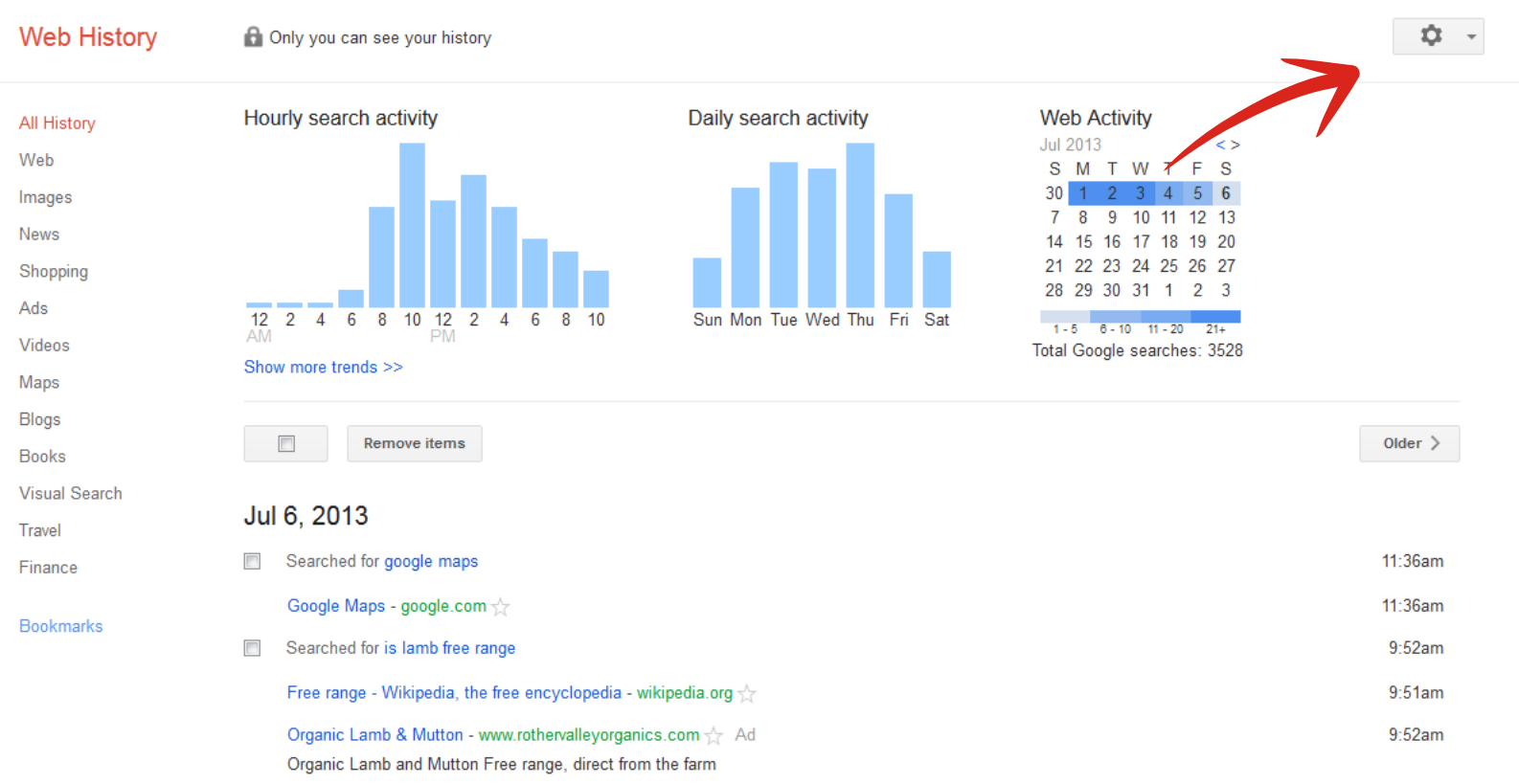
To turn Search History off, click on the gear icon on the top right, and select ‘Settings’…
the weakness in the way in which SSL is commonly implemented.
However, all this is no good if the email service is simply handing over your information to an adversary (asGoogle and Microsoft have been doing with the NSA). While it seems that smaller email providers have not (yet) been affected, it is likely that as the NSA and other national government surveillance organizations extend their reach, this will change.
The answer to this problem lies in end-to-end email encryption, where the sender encrypts the email, and only the intended recipient can decrypt it. The biggest problem with using an encrypted email system is that you cannot impose it unilaterally – your contacts, both recipients and senders, also need to play ball for the whole thing to work, and while trying convincing your granny to use PGP encryption will likely just lead to bafflement, trying to convince your customers might make many of them very suspicious!
It should also be noted that email encryption does not encrypt everything. The email addresses of sender and recipient, date and time of sending, and the e-mail’s subject line are not encrypted; just the body and any attachments. As we briefly discussed earlier, metadata such as this can still be very damaging in the wrong hands.
Another point worth bearing in mind if you are worried about NSA spying is that, probably even more than encrypting other aspects of your internet use, encrypting your email is pretty much asking for the NSA to store your emails ready for decryption when they are able to do so.
Pretty Good Privacy (PGP, which was once open source and free, but is now the property of Symantic). The Free Software Foundation has taken up the open source OpenPGP banner however, and with major funding from the German government has released GNU Privacy Guard (also known as GnuPG or just GPG).
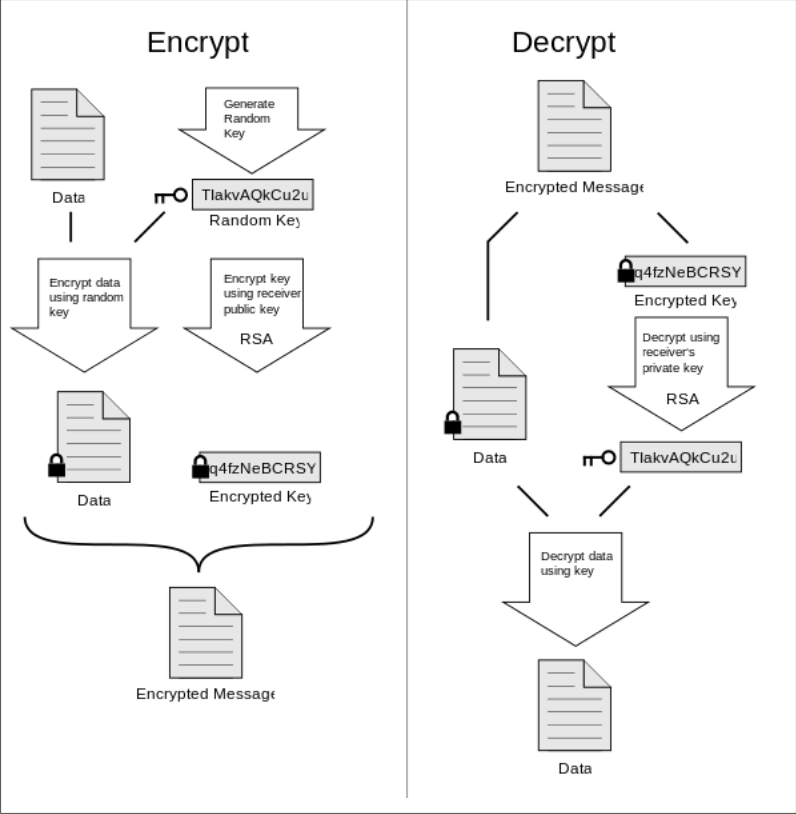
An overview of how the OpenPGP standard works
Following the OpenPGP standard and fully compatible with PGP, GnuPG is a free and open source alternative which is available for Windows, OSX and Linux. Although the basic program uses a simple command line interface, more sophisticated versions are available for Windows (Gpg4win) and Mac (GPGTools). Alternately,EnigMail adds GnuPG functionality to the Thunderbird and SeaMonkey email clients. We have written a full guide to setting up GnuPG in Windows using Gpg4win, available here.
https://play.google.com/store/apps/details?id=info.guardianproject.gpg&feature=related_apps#?t=W251bGwsMSwxLDEwOSwiaW5mby5ndWFyZGlhbnByb2plY3QuZ3BnIl0. from the Guardian Project is available from the Play Store., and although we have not tried them, mobile users wanting a more user-friendly experience may want to give K-9 Mail (a well-regarded email client with PGP support built-in) combined withhttps://code.google.com/p/android-privacy-guard/ (Android), or iPGMail (iOS) a try. A good guide for getting GPG working on Android is available http://geekyschmidt.com/2010/12/09/gpg-on-your-android-phone.
Hushmail was considered the go-to service for secure webmail, as it offered PGP encryption in a web based service. However, in 2007 a backdoor was used by the owners to capture emails of three accounts, which were then handed over to the Canadian Courts. As Hushmail CTO Brian Smith said in refreshingly honestblog post,
‘[Hushmail] is useful for avoiding general Carnivore-type government surveillance, and protecting your data from hackers, but definitely not suitable for protecting your data if you are engaging in illegal activity that could result in a Canadian court order.’
It should be noted that any web-based service can in theory be compelled to modify their system to capture users’ decryption keys (as Hushmail did), and Hushmail itself recommends using non web-based services such as GnuPG or PGP Desktop if stronger security is needed.
https://addons.mozilla.org/en-US/firefox/addon/encrypted-communication/we’ve written a guide about how to use it) which provides 256-bit AES end-to-end encryption. Once the extension is installed, just write your email, right-click anywhere in the text of the message and select ‘Encrypted Communication’ to encrypt it. You will be asked to enter a password, which the recipient will need to know (along with having the extension running on their Firefox) to decrypt the message. Of course, you should transmit this password to the recipient using a different communication method than email (in person is best, but encrypted VoIP or messaging should be fine – see below)!
Even more secure is Mailvelope, which provides full end-to-end OpenPGP encryption over web email services such as Gmail, Hotmail, Yahoo! and GMX using Firefox or Chrome. We have a full guide to using it availablehere.
Note that there are other extensions available which seem to offer similar functionality and which we often see recommended on the internet, but which should be avoided. Both https://chrome.google.com/webstore/detail/safegmail/lmjkmpdndmbieflefonjgnnfimmkbedf?utm_source=chrome-ntp-icon for Chrome and Enlocked(multiplatform) send your email to their servers for decryption, which means that it at least as vulnerable as mail sent to Hushmail (i.e. they do not offer end-to-end encryption). Furthermore, the SafeMail decryption page is not even SSL encrypted!
elsewhere, but it is worth briefly noting here that if it is just files you wish to protect, these can be encrypted before sending them by regular email.
It is also possible to encrypt stored emails by encrypting the email storage folder using a program such as TrueCrypt (discussed later). explains where Thunderbird stores emails on different platforms (for example).
metadata, and it is also totally pointless unless the people you are calling are equally paranoid.
as happened with Skype) or some other government origination, this security is next to meaningless.
So, as with email, what is needed is end-to-end encryption where an encrypted tunnel is created directly between the participants in a conversation, and no-one else.
Jitsi (Windows, OSX, Linux, Android (experimental)) – this free and open source software offers all the functionality of Skype, including voice calls, video conferencing, file transfer and Chat, but can encrypt it all with ZRTP. The first time you connect to someone it can take a minute or two to set up the encrypted connection (designated by a padlock), but is afterwards transparent. As a straight Skype replacement, Jitsi is difficult to beat
Ditch the cell phone!
While we are on the subject of phones (sort of), we thought we should also mention that when you carry your phone, your every movement can be tracked. It’s not just things like GPS and Google Now (which works uncannily well at predicting what you want by storing just about every piece of data about you) on Smartphones – even the most modest cell phone can be easily tracked by the phone towersit uses to work. The only solution, if you really don’t want to be tracked, is to leave your phone at home (or buy one of these). Incidentally, the Google Now service only works effectively if Goggle History is turned on (see above).
reserve the right to investigate your files and hand them over to the authorities if they receive a court order.
To ensure that your files are secure, there are a number of basic approaches you can take (note that the options discussed below are far from the only ones available, as this is a highly competitive market space where many new and innovative solutions are appearing all the time)…
http://www.bestvpn.com/wp-admin/post.php?post=7096&action=edit&message=1#truecrypt. This has the advantage that you can carry on using your favorite Cloud storage service, no matter how inherently insecure it is, as you hold all the encryption keys to your files.
The downside compared to services such as SpiderOak and Wuala (see below), is that you don’t get access to your files on the go.
here.
If you are in the market for a good Dropbox alternative, you may like to check out BestVPN’s sister websiteBestBackups, for news and reviews of the best and the rest when it comes to cloud storage services.
Use an automatically encrypted cloud service
These services automatically encrypt files before uploading them to the Cloud (we have no truck with any service that encrypts files server-side, as these are always vulnerable to being decrypted by the service provider). Any changes to files or folders are synced with local decrypted versions before being secured and sent to the Cloud.
Both SpiderOak and Wuala have iOS and Android apps, so you can easily sync across all your computers and mobile devices. This convenience comes at a small security price, as both services briefly store your password on their servers to authenticate you and direct you to your files. Wuala also uses this password to encrypt and decrypt your files when using a mobile device, although this is somewhat compensated for by Wuala uploading different segments of your files to different servers, making it impossible for them to identify which data belongs to which user. In both cases the passwords are deleted once a session is finished.
Because of its high profile, we feel that Kim Dotcom’s Mega service deserves a special mention, particularly as it offers a very generous 50GB encrypted space for free. Mega uses your web browser to encrypt files before uploading and decrypt them after downloading, which is great for convenience (and an Android app is available, with an iOS one on the way), but is not as secure as the other methods outlined here.
Our feeling therefore, is that while it is worth paying attention to how Mega deals with its security issues, it is probably best avoided for the time being. It is also worth pointing out that Kim Dotcom’s involvement ensures the service receives the highest possible level of scrutiny from security, law enforcement and copyright enforcement bodies the world over.
BitTorrent Sync service is now in public beta phase (i.e. it is available to the public, but is still considered experimental). Designed more or less as a Dropbox replacement, BitTorrent Sync synchronizes files and folders across devices, but does so without storing them in ‘the Cloud’.
You chose a folder that you want to share, and BitTorrent Sync gives you a secret for it. You can then link that folder to a folder on another device (with BitTorrent installed on it) using the secret. Any number of additional folders can be added in a similar fashion, and all files are transferred using a securely encrypted (256-bit AES) P2P protocol.
BitTorrent Sync is free, easy to use, and is currently available for Windows, OSX , Linux and Android (with an iOS app in private alpha stage). A limitation of the system is that as it is not a cloud service, it cannot be used as an extra drive by portable devices with limited storage, but on the plus side you are using your own storage, and so are not tied to Cloud providers’ data limits (or charges).
pulled the plug on the popular full-disk encryption program. Conspiracy theories abound, and while some developers seek to fork the software, Phase II of the audit goes ahead. For more details on the story see here and here. Until the audit is complete, we strongly suggest avoiding TrueCrypt, and migrating TrueCrypt containers to other programs, such as to https://diskcryptor.net/wiki/Main_Page for Windows users, or https://code.google.com/p/cryptsetup/ and bwalex/tc-play (a free TrueCrypt Implementation based on dm-crypt) for Linux users.
While other solutions are of course available, the king of local encryption is undoubtedly the powerful free/donationware, open source program TrueCrypt(available on Windows, OSX and Linux).

TrueCrypt can be used to create encrypted volumes on your computer, to encrypt entire disks, to create hidden volumes, and even to create an entire hidden operating system (using 256-bit AES, or any of a number of user specified encryption schemes). What makes Truecrypt so powerful and easy to use is on-the-fly encryption, which allows you to work with files as you would on normal, unencrypted files, without the hassle of continually encrypting and decrypting them. Once a volume is mounted (using a password), then operation is transparent, with TrueCrypt keeping temporary files in RAM. and generally cleaning up after itself once a session is finished.
For ultimate security, you can encrypt the drive your operating system is installed on, which will ensure that all the little system files and other bits of junk that OS’s tend to create remain secure. Of course, if you forget your password then you won’t be able to boot into your system! TrueCrypt will also even let you create a container with hidden Operating System in it (see below)!
TrueCrypt allows you to create hidden volumes, which provides’ plausible deniability’ as it is impossible to prove that a second volume exists. This is great in situations where guilt must be proven, but also means that if this is not the case (e.g. in repressive countries where innocence must be proven), it is impossible to prove a hidden volume does not exist either (which may result in imprisonment or torture based on the assumption that it does exist!). We have written a post on this subject examining the issue in more depth.
crowdfunded project to properly audit TrueCrypt’s code has now been completed, and the results are somewhat worrying. ‘iSEC found no evidence of backdoors or otherwise intentionally malicious code in the assessed areas,’ but some very sloppy code was discovered that ‘did not meet expected standards for secure code.’
This is hardly encouraging given the massive resources that the NSA deploys to uncover just such weaknesses, and leads us to worry that these flaws have already been discovered by them. Nevertheless, TrueCrypt remains the best encryption method available, and was enough to see off the police in the http://www.reuters.com/article/2013/08/30/us-usa-security-snowden-nytimes-idUSBRE97T0RC20130830.
Cyrptonite brings TrueCrypt and http://www.arg0.net/encfs to Android, including allowing users to access TrueCrypt containers (if you experience problems, a command line version of TrueCrypt is included with the app). EDS Lite is another good option that does more or less the same.
Unfortunately there is no TrueCrypt compatible app or alternative available for iOS devices that we are aware of.
Part 1 Part 2.
Alternatives to Truecrypt
If the the auditing results for TrueCrypt or the implications of ‘plausible deniability’ worry you, there are a couple of other highly regarded encryption programs available:
Use antivirus, anti-malware and firewall software
BestAntivirus.com. If you would like to choose an antivirus package that best fits your needs, please take the time to check it out! Now, back to the guide…

It almost goes without saying, but as this is an ‘ultimate guide’ we’ll say it anyway… always use anti-virus software and make sure that it is up-to-date!
Not only can viruses really screw up your system, but they can let hackers enter it, giving them access to all your (unencrypted) files and emails etc., webcam, passwords stored in Firefox (if no master password is set), and much more. Keyloggers are particularly dangerous as they can be used to access bank details and track pretty much everything you do on your computer.
It is also worth remembering that not just criminal hackers use viruses! The Syrian government, for example, launched a virus campaign known as Blackshade, aimed at ferreting out and spying on political dissidents.
Although most people are aware they should be using anti-virus software on their desktop computers, many neglect their mobile devices. While there are less viruses targeting mobile devices at present, smart phones and tablets are sophisticated and powerful computers, and as such are vulnerable to attack by viruses, and should therefore be protected.
Mac users are famously bad for not installing ant-virus software, citing the ‘fact’ that OSX’s Unix architecture makes virus attacks difficult (this is hotly contested by the way), the fact that most hackers concentrate on Windows because most computers use Windows (true), and the anecdotal evidence of many Mac users who have gone for years without using anti-virus software yet never experienced any problems. However as events last year demonstrated, Macs are not immune to viruses, and anyone serious about their security should always use good anti-virus software.
consensus is that free antivirus software is as good at preventing viruses as paid-for alternatives, but paid-for software provides better support and more comprehensive ’suites’ of software that are designed to protect your computer from a range of threats (combining antivirus, anti-phishing, anti-malware and firewall functions for example). Similar levels of protection are available for free, but require the use of various different programs. Also, most free software is for personal use only, and businesses are usually required to pay for a license.
Some good anti-virus software:
Comodo Firewall Free and ZoneAlarm Free Firewall 2013, which are good free options
Unfortunately, despite great strides made in the right direction, Linux remains less user friendly than either Windows or OSX, and less computer literate users may struggle with it. If you are serious about privacy however, Linux really is the way forward, and one of the best things about it is that you can run the entire OS from a Live CD, without the need to install it. This not only makes it easy to try out different Linux distros, but also adds an extra layer of security when you access the internet.
Ubuntu is very popular due to the fact that it is one of the easiest Linux distros to use, and thanks to this popularity there is a great deal of assistance available for it from an enthusiastic Ubuntu community. It therefore makes a good starting point for those interested in a using a much more secure Operating System.
More experienced users however might want to take a look at Tails, a Linux distro built from the ground up to preserve privacy and anonymity, and which forces all connection to go through Tor.
Puppy can help, as does installing the VM on a separate hard drive to your main OS.
Popular VM software includes the free VirtualBox and VMWare Player, and the premium ($273.90) enterprise level VMware Workstation. As noted above, TrueCrypt lets you encrypt an OS, or even hide one.
VirtualBox Virual Machine, and ensures that DNS leaks are not possible, and that ‘not even malware with root privileges can find out the user’s real IP’.
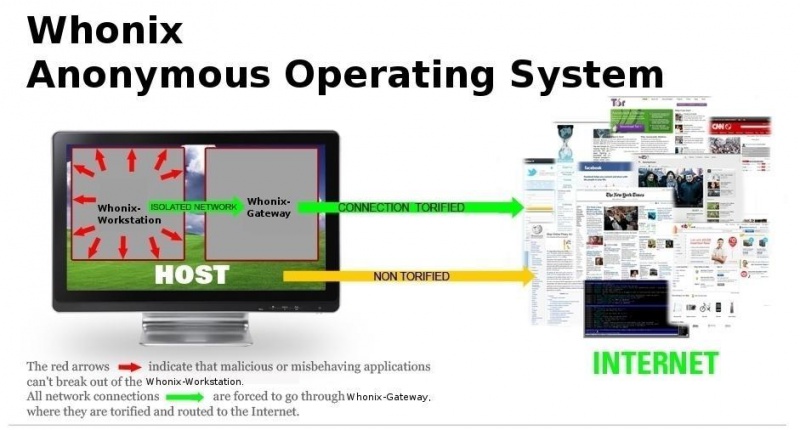
It consists of two parts, the first of which acts as a Tor gateway (known as Whonix Gateway), while the second (known as a Whonix Workstation) is on a completely isolated network which routes all its connections through the Tor gateway. This isolation of the workstation away from the internet connection (and all isolated from the host OS inside a VM), makes Whonix highly secure.
insecure piece of software (see also Flash Cookies), but despite the gains made by HTML5, it remains an important part of most people’s internet user experience. It is therefore a good idea to check its settings, and turn off most of them off (paying particular attention to the Camera and Mic settings!).
Many security related browser plugins disable Flash by default, which a good thing, but does not help when you actually want view the Flash content. Be careful however to only allow Flash on trusted websites. The Flash Player Settings Manager has moved from being online to being accessed locally, and the easiest way to open it is to right-click on some Flash content (e.g. a YouTube video) and select ‘Global Settings…’.
www.bestvpn.com to its IP address of 216.172.189.144, the Domain Name System (DNS) is used.
By default this translation process is performed on your ISP’s DNS servers, which ensures your ISP has a record of all websites you visit. Even when using a VPN service (highly recommended), possible DNS leakage may result in your ISP handling this DNS translation instead of your VPN provider (as should happen).
Fortunately, there are a number of free and secure public DNS servers, including OpenDNS and Comodo Secure DNS, although we prefer the non-profit, decentralized, open, uncensored and democratic OpenNic(which we discuss here). We recommend changing your system settings to use one these instead of your ISP’s servers, and have instructions of how to do this in Windows 7 (along with a guide on how to detect and block DNS leaks when using a VPN) available here.
DNS was not built with security in mind and it is vulnerable to a number of attacks, the most important of which is a ‘man-in-the-middle’ attack known as DNS spoofing (or DNS cache poisoning), where the attacker intercepts and redirects a DNS request. This could, for example, be used to redirect a legitimate request for a banking service to a ‘spoof’ website designed to collect account details and passwords for unsuspecting victims.
This has prompted the chaps at OpenDNS to develop http://www.opendns.com/technology/dnscrypt/, a lightweight program that encrypts ‘all DNS traffic between the user and OpenDNS, preventing any spying, spoofing or man-in-the-middle attacks’. Using Curve25519 elliptical-curve cryptography, DNSCrypt is available for Windows, OSX and Linux, and although in ‘preview release’ stage, is considered stable. The only issue is that OpenDNS is run by a private company (which is why we prefer OpenNic), but it is currently the only program of its kind available.
set a master password to prevent just anyone peeking at your passwords in Firefox’s options dialogue. In addition to this, it is probably a god idea to back up your Firefox passwords every now and again
While other countries’ governments’ seem desperate to increase their own control over their citizen’s data, nothing (including China’s attempts at internet surveillance) matches the scale, sophistication or reach of PRISM.
It is therefore a very good idea, if such things worry you (as they should), to avoid all dealings with US companies where you are concerned about your privacy. To suggest that every US company may be complicit in handing every user’s personal information over to a secretive and largely unaccountable spying organization might sound the stuff of paranoid science fiction fantasy, but as recent events have proved, is terrifyingly close to the truth…
Note also that due to provisions in both the Patriot Act and the Foreign Intelligence Surveillance Act (FISA), US companies must https://www.bestvpn.com/blog/9620/us-forces-microsoft-to-hand-over-emails-stored-in-ireland/ even if that user is a non-US citizen, and the data has never been stored in the US.
In addition to this, the UK’s GHCQ is in bed with the NSA and carries out some particularly https://www.bestvpn.com/blog/8893/ghcq-grabs-millions-of-often-explicit-yahoo-webcam-images/spying projects of its own (‘They [GCHQ] are worse than the US’, Edward Snowden). Indeed, all members of the English speaking ‘Five Eyes‘ spying alliance (US,UK, Canada, Australia and New Zealand) share information between their security organizations and use each other to spy on their own citizens (to bypass national laws prohibiting this), and so companies based in these countries should also be similarity avoided.
Google Now is an excellent case in point. An ‘intelligent personal assistant’, this software’s ability to anticipate what information you require is uncanny. It can, for example remind you that you need to leave the office to catch the bus ‘now’ if you want to get home at your usual time, as well as providing navigation to the nearest bus-stop, and alternative timetables should you miss it. Google’s new, and possibly game-changing Google Glass system makes heavy use of Google Now technology, which relies on storing and curating large amounts of information about your habits, likes, dislikes, browsing history, where you like to drink, and much more.
In other words, some of the most exciting and interesting developments in human-computer interaction rely on a full-scale invasion of our privacy, and to box yourself in with encryption and other privacy protection methods is to reject the possibilities afforded by these new technologies.
We mainly pose the question ‘is privacy worth it’ as food for thought. Privacy comes with a cost, and it is worth thinking about what compromises you are willing to make, and how far you will go, to protect it. In our view privacy IS vitally important, as everyone has a right not to have almost every aspect of their lives recorded, examined and then judged or exploited (depending on who is doing the recording), but it has to be recognized that maintaining privacy is not easy (and can never be completely guaranteed) in the modern world.
Of course, what most of us probably want is the ability to share what we want with our friends and with services that improve our lives, without worrying this information is being shared, dissected and used to profile us for dubious ends. While this is not likely to happen soon, if more people make even fairly basic efforts to improve their security, it would make both government agencies’ and advertisers’ jobs much more difficult, to the point that it could even force a change of approach.
https://opentrackers.org/educateyourself/.
https://darknetmarkets.org/guides/the-ultimate-online-privacy-guide/
Ladies and Gentlemen, here it is. We’ve put a lot of effort into this, and it’s very long. We tried to think of every angle in terms of privacy, and the effort was worth it. Almost 13,000 words about how to protect your privacy online. There’s no need to read it at once, just check the index below and click on the parts that interest you.
Update 08 May 2014: in addition to many minor updates, we have included a whole new section on the Heatbleed Bug, have completely revamped the section on Encryption to better reflect the ongoing revelations about the NSA’s concerted attempt to subvert all encryption standards (possibly with NIST help), and have noted the results of the first phase of the ongoing audit of TrueCrypt.
Update 17 June 2014: in a move that is as surprising as it is baffling, the devs behind TrueCrypt have pulled the plug on the popular full-disk encryption program. Conspiracy theories abound, and while some developers seek to fork the software, Phase II of the audit goes ahead. For more details on the story see here and here. Until the audit is complete, we strongly suggest avoiding TrueCrypt, and migrating TrueCrypt containers to other programs, such as to https://diskcryptor.net/wiki/Main_Page for Windows users, or https://code.google.com/p/cryptsetup/ and bwalex/tc-play (a free TrueCrypt Implementation based on dm-crypt) for Linux users.
Index
Introduction
So how secure is encryption?
- Encryption key leghth
- Ciphers
- NIST
- NSA attacks on key encryption
- Perfect Forward Secrecy
- The takeaway – or So is encryption secure?
- The importance of end-to-end encryption
- Metadata
Use Foss Software
Pay for stuff anonymously
Anonymise your internet use
Secure your browsing
- Cached DNS entries
- Flash Cookies
- Other web tracking technologies
- Great browser extensions you should use
- Block reported attack sites and web forgeries in Firefox
- Mobile browser security
Secure your email
- Encrypt your emails using GNU Privacy Guard
- PGP on mobile devices
- Encrypted Webmail
- Encrypt your Gmail
- Other email precautions
- VoIP with end-to-end encryption
- Secure your text messages, Instant Messaging and Chat
- Ditch the cell phone!
- Manually encrypt your files before uploading them to the cloud
- Use an automatically encrypted cloud service
- Use BitTorrent Sync Cloudless syncing
Use antivirus, anti-malware and firewall software
Miscellaneous security hints and tips and tricks
- Use Linux rather than a commercial OS
- Use a Virtual Machine
- Give Whonix a try
- Password protect your BIOS
- Secure your Flash Player settings
- Change DNS servers
- Use secure passwords
- Social networking
- Avoid all US based services
http://www.guardian.co.uk/world/interactive/2013/jun/20/exhibit-b-nsa-procedures-document, but what it boils down to is that data from US citizens is examined, and then discarded if found to be uninteresting to the NSA. Encrypted data on the other hand is stored indefinitely, until such time as the NSA can decrypt it. All data relating to non-US citizens can be kept indefinitely, but sheer practicality suggests that encrypted data gets special attention.
If a lot more people start to use encryption, then encrypted data will stand out less, and surveillance organizations’ job of invading everyone’s privacy will be made much lot harder. Remember – anonymity is not a crime!
scale of the NSA’s deliberate assault on global encryption standards and the on-going fiasco that is the Heartbleed Bug, confidence in encryption is not as high as it was just a few months ago, so let’s examine the current state of play…
require 3.4 x10(38) operations to reliably break
- In 2011 the fastest supercomputer in the word (the Fujitsu K computer located in Kobe, Japan) was capable of an Rmax peak speed of 10.51 petaflops. Based on this figure, it would take Fujitsu K 1.02 x 10(18) (around 1 billion) years to crack a 128-bit AES key by force
- In 2014 the most powerful supercomputer in the world is the NUDT Tianhe-2 in Guangzhou, China. Almost 3 times as fast as the Fujitsu K at 33.86 petaflops, it would ‘only’ take it around a third of a billion years to crack a 128-bit AES key. That’s still a long time, and is the figure for breaking just one key
- A 256-bit key would require 2(128) times more computational power to break than a 128-bit one
- The number of operations required to brute force a 256-bit cipher is 3.31 x 10(65), a number roughly equal to the number of atoms in the universe!
It should be noted that the US government uses 256-bit encryption to protect ‘sensitive’ data (and 128-bit for ‘routine’ encryption needs). However the method it uses is AES, which as we shall discuss below is not without problems.
Heartbleed Bug.
NIST
works closely with the NSA in the development of its cyphers. Given what we now know of the NSA’s systematic efforts to weaken or built back doors into international encryption standards, there is every reason to question the integrity of NIST algorithms.
Although NIST has been quick to deny any wrong doing (‘NIST would not deliberately weaken a cryptographic standard’), and has invited public participation in a number of http://csrc.nist.gov/publications/PubsDrafts.htmlin a move designed to bolster public confidence, the New York Times has accused the NSA of circumventing the NIST approved encryption standards by either introducing undetectable backdoors, or subverting the public development process to weaken the algorithms.
Any existing trust was pretty much destroyed by news that a NIST certified cryptographic standard – the Dual Elliptic Curve algorithm (Dual_EC_DRGB) had been deliberately weakened not just once, but twice, by the NSA.
That there might be deliberate backdoor in Dual_EC_DRGB had already been noticed before. In 2006 researchers at the Eindhoven University of Technology in the Netherlands noted that an attack against it was easy enough to launch on ‘an ordinary PC’, and Microsoft engineers flagging up a suspected backdoor in the algorithm. Despite these concerns however, where NIST leads, industry follows, and Microsoft, Cisco, Symantec and RSA all http://csrc.nist.gov/groups/STM/cavp/documents/drbg/drbgval.html, in large part due the fact that compliance with NIST standards is a prerequisite to obtaining US government contracts.
When you consider that NIST certified cryptographic standards are pretty much ubiquitous worldwide throughout all areas of industry and business that rely on privacy (including the VPN industry), this is all rather chilling. Perhaps precisely because so much relies on these standards, cryptography experts have been unwilling to face up to the problem – at least until Silent Circle, the company which closed its Silent Mail service rather than see it compromised by the NSA, announced in November 2013 that it planned to https://www.bestvpn.com/blog/7703/silent-circle-moves-away-nist-encryption-standards/.
NSA attacks on RSA key encryption
revelations that came out of the new information provided by Edward Snowden in September is that, “another program, codenamed Cheesy Name, was aimed at singling out encryption keys, known as ‘certificates’, that might be vulnerable to being cracked by GCHQ supercomputers.”
That these certificates can be ‘singled out’ strongly suggests that 1024-bit RSA encryption (commonly used to protect the certificate keys) is weaker than previously thought, and can be decrypted much more quickly than expected by the NSA and GHCQ. Once a certificate key has been decrypted, then all exchanges past and future will be compromised if non ephemeral key exchange is used (i.e. if, as is depressingly common practice, a single permanent private key is used to decrypt all data).
This means that many forms of encryption which rely on certificates and non ephemeral keys must be regarded broken, including SSL and TLS. This has huge implications for all HTTPS traffic.
The good news is that OpenVPN, which uses ephemeral (temporary) key exchanges, should not be affected. This is because with ephemeral key exchanges a new key is generated for each exchange, and there is therefore no reliance on certificates to establish trust. Even if an adversary were to obtain the private key of a certificate, they could not decrypt the communication. It is possible that a man in the middle (MitM) attack could target an OpenVPN connection if the private key has been comprised, but this would have to be specifically targeted attack. Unfortunately, OpenVPN uses the OpenSSL library, and may be vulnerable to Heartbleed.
Since news that the NSA (and GHCQ) can crack 1028-bit RSA encryption became public, some VPN providers at least have beefed up their key encryption to 2048-bits, or even up to 4096-bits.
Perfect Forward Secrecy
perfect forward secrecy, a system whereby a new and unique (with no additional keys derived from it) private encryption key is generated for each session. (i.e. use of ephemeral key exchanges).
Although still in the minority, more companies are beginning to use ephemeral keys, and those which do are largely immune to the Heartbleed Bug.
The takeaway – or So is encryption secure?
It is becoming abundantly clear that to underestimate the NSA’s ambition or ability compromise all encryption is a bad mistake. However, it remains the best defence we have against them (and others like them), and to the best of anyone’s knowledge strong ciphers such as AES (despite out misgivings about its NIST certification) and OpenVPN (once patched against the Heartbleed bug) remain secure.
As Bruce Schneier, encryption specialist, fellow at Harvard’s Berkman Center for Internet and Society and privacy advocate says,
‘Trust the math. Encryption is your friend. Use it well, and do your best to ensure that nothing can compromise it. That’s how you can remain secure even in the face of the NSA.’
It is also worth remembering that the NSA is not the only potential adversary, and most criminals and even government organisations have nowhere near as much ability to circumvent encryption as the NSA does.
The importance of end-to-end encryption
inspection by the NSA.
Basically, services that encrypt your data on their servers, rather than you encrypting your own data on your own machine, should be strongly avoided.
Metadata
powerful tool in the wrong hands (i.e. just about anybody).
For example, even if using a securely encrypted end-to-end voice service such as Silent Circle, your ISP (and anyone else watching) will still be able to tell who you are making the call to, whether you are calling from your usual location, how often you call, how long you usually chat, and much more. With such information it would be trivially easy to discover that you were having an affair (for example)…
However, the reason we said ‘not necessarily protect users’ is that technologies such as VPN and Tor do make the collection of metadata very difficult. In the example above, if you always connected to a VPN service when using the internet, all a watcher could tell is that you are connected to a VPN server, not that that you are using Silent Circle, let alone where and when you are using it…
Although the NSA does target individual communications, its primary concern is the collection of metadata.
https://www.bestvpn.com/blog/9430/did-the-nsa-know-about-the-heartbleed-bug/ in the open source code of OpenSSL versions 1.01 through 1.0.1f (inclusive), represents perhaps the most ‘catastrophic’ threat to online security yet.
OpenSSL is by far the most commonly used cryptographic library on the internet, used by banks, VPN companies, online storage services – basically almost everything that requires a secure internet connection, and it is estimated that over two thirds of the internet was affected by the bug which went unnoticed by the cryptographic community for almost a year and half.
Even worse, if a system has been compromised using the Bug there is no way to know about it, and given the huge amounts of resources the NSA has at its disposal to discover such cryptographic weaknesses, it is likely that it, at the very least, https://www.bestvpn.com/blog/9430/did-the-nsa-know-about-the-heartbleed-bug/ about the bug but didn’t bother to tell anyone.
By exploiting the bug an attacker can access users’ accounts, steal their passwords, and even https://www.bestvpn.com/blog/9445/heartbleed-can-be-used-to-steal-ssl-keys/. Yup, disastrous is the word! Hopefully most websites and services using the vulnerable versions of OpenSSL (ones using older versions were not affected) have updated their OpenSSL libraries to patch the vulnerability, plus re-issued their SSL certificates as these may have been compromised. Unfortunately this may be a somewhat forlorn hope, as at the time of writing almost half of the servers believed to be vulnerable in the days immediately following the Heartbleed disclosure remain susceptible.
Being sure that companies have done this is difficult however, and so far . A number of online tools are available to test servers for vulnerability to Heartbleed, but as this report details, these may not be completely reliable.
The whole mess is compounded by the fact that many companies claim to have fixed the problem simply because they have patched the vulnerability, but have not changed their SSL certificates. This is a bit like putting a fancy padlock on a glass door, as if they have already been compromised and the attacker already has access to the SSL certificates, they will still have full access the server.
If you are unsure about whether a particular service has properly fixed the problem, the best thing you can probably do is to contact them and ask what the situation is.
Most of the fixing is a server-side issue, and there is nothing you can do as a user, but once fixed it is essential that you change your passwords immediately! If a server has been compromised at any time over the last year and half the attacker will have your password, and if you use that password on more than one site, they can use it to compromise even services that were unaffected by the Heartbleed Bug.
What this means is that by now you should change your all your passwords (although if you change your password before a site has completely fixed all Heartbleed issues then it is still potentially vulnerable to hackers).
See our section in this Guide on how to make your passwords more secure. Ideally you should use a different password for every service and website you use (at least the important ones), so a password manager program may be the best solution.
One final note is that websites which have had the foresight to to implement Perfect Forward Secrecy are largely unaffected by the Heartbleed Bug, even if using a compromised version of OpenSSL.
no proprietary software can be trusted; even software specifically designed with security in mind. It is now a proven fact that the NSA has co-opted or coerced hundreds of technology companies into building backdoors into their programs, or otherwise weakening security in order to allow the NSA access. US and UK companies are particularly suspect, although the reports make it clear that company’s across the world have acceded to NSA demands.
The problem with proprietary software is not just that as sole developers and owners, companies can be fairly easily approached and convinced to play ball with the NSA, but that their source code is kept secret, making it easy to add to or modify in dodgy ways without anyone noticing.
The best answer to this problem is to use free open source software (FOSS). Often jointly developed by disparate and otherwise unconnected individuals, the source code is available to everyone to examine and peer-review, thereby minimizing the chances that it has been tampered with. Ideally this code should also be compatible other implementations, in order to minimize the possibility of a back-door being built in.
It is of course possible that NSA agents have infiltrated open source development groups and introduced malicious code without anyone’s knowledge, and the sheer amount of code that many projects involve means that it is often almost impossible to fully peer-review all of it. Still, despite these potential pitfalls, FOSS remains the most reliable and least likely to be tampered with software available, and if you truly care about privacy you should try to use it exclusively (up to and including using FOSS Operating Systems such as Linux).
Mullvad, will even take cash sent anonymously in the post.
5 Best VPNs that accept Bitcoin!) that aim to improve users’ anonymity,
One important thing to understand is that Bitcoin is not inherently anonymous. The exciting thing is that with care it can be made so.
Buying Bitcoins Anonymously
Most Bitcoin traders are located in the US and have US based bank accounts, which can make buying Bitcoins outside the States both a little involved, and location dependent. However, the following methods are common ways to obtain Bitcoins anonymously.
For maximum anonymity:
- Use anonymous, disposable email addresses (such as those supplied by Tor Mail)
- Create a new Bitcoin address (wallet) for each purchase – if you use the same address then one mistake will allow all transactions to be traced back to you
- Never reveal personal information such as your real name, address, or phone number
- Use a mixer service – even if you use one of the more anonymous methods of purchasing Bitcoins outlined below, it can’t hurt to launder it further (although this will cost a bit).
Neither the cheapest nor the most anonymous method, this is the most convenient, and does nevertheless ensure a high degree of anonymity. Using this method you do not actually buy your Bitcoins anonymously; you simply purchase them from an automated Bitcoin exchange (such as CoinBase), and then ‘launder’ them using a ‘mixer’ service such as Blockchain.info Shared Send.
A mixer service basically anonymises your Bitcoins by swapping them with multiple other users, making it very difficult (but not impossible for a determined investigator) to follow the chain back to you. Services such as this are, of course, not free (Blockchain.info for example charges a 0.5% fee).
Many automatic exchanges require you to prove your real world identity, in which case it is easy to determine that you have purchased Bitcoins (but not what happens to them after that if you mix them).
2. Use pre-paid credit cards
This method is somewhat location dependent, but in most areas it is possible to buy pre-paid ‘gift’ credit cards over-the-counter, which can then be used to buy Bitcoins anonymously if the transaction is performed through disposable email addresses etc. Alternatively, you can just use the card to buy an on-line service directly!
3. Buy locally with cash
The website LocalBitcoins.com lets you find Bitcoin sellers who live near you. Once you have found a seller you are happy with, it is up to you to contact them and to arrange a meeting.
Prices are generally higher than those on Mt Gox, and you should pay attention to the feedback to ensure the seller is highly scored (it works much like the feedback system on eBay).
4. Buy from an individual seller online
This can be done on LocalBitcoins.com, or in the #bitcoin-otc chatroom on Freenode (otc = over-the -counter).
#bitcoin-otc uses a quite involved feedback system, which it is well worth spending the time to understand, and you will need to hash out the payment method with the seller. A list of IRC client can be found here.
here, and some of the pros and cons of the ‘top 5’ are outlined in this article.
We have written an extensive guide to buying and paying for VPN (although the same principles apply to any service of course) anonymously using Bitcoins, starting here.
this article, but to summarize…
Mullvad, AirVPN and Private Internet Access (although the fact that PIA is US based has introduced considerable uncertainty to this recommendation).
Pros:
- As long as your VPN provider is trustworthy and keeps no logs, VPN is a very secure and anonymous means of surfing the internet
- It is also good for securing connections at public WiFi hotspots, and for evading firewalls used to censor the internet
- It is a lot faster than Tor (although there will be a small hit to your internet speeds)
- It is very good for P2P filesharing, and ‘spoofing’ IPs in order to stream geo-restricted media content (e.g. Hulu).
- It relies on trusting your VPN provider, and is therefore not as secure as Tor
- It costs money (typically between $7 to $10 per month, with substantial discounts for bulk purchases). Many VPN providers accept Bitcoin payments.
- It is obvious to observers that you are using VPN.

The final link in the chain, the one that connects you to the internet, is known as an exit node, and is one of the biggest weaknesses of the system. Nodes are run by volunteers, and those running exit nodes are vulnerable to prosecution over the behaviour of other Tor users who have used the system for illegal purposes (including piracy and much worse), as the IP of the offenders can been traced to the exit node’s IP address.
This has led to a fairly small number of public exit nodes being available, and has meant that restrictive governments such as China, who monitor these nodes, have been able to block access to many of them. There are still plenty of nodes around however, but it does mean that Tor users in some countries my need to reconnect to a number of different nodes before they find one that has not been blocked.
The other big problem with Tor is that it is very slow, as users’ data is routed through a number of servers randomly located anywhere in the world before connecting to the internet.
Pros:
- Very secure and anonymous (in fact it is generally considered the most secure and anonymous way to access the internet available, and is therefore suitable for political dissidents and the like)
- It is also good for securing connections at public WiFi hotspots and for evading firewalls used to censor the internet (although see comments blocked exit nodes above)
- Free
- Slow (often very)
- Restrictive countries can make finding unblocked public exit nodes a pain
- Not good for P2P downloading and streaming from spoofed IPs – not only are network speeds too slow for this to be practical, but doing so slows down the system even more for other users. In addition to this, volunteers running the exit nodes may be held accountable for your copyright violations, so it is considered very rude
- It is obvious to observers that you are using Tor, and some websites (such as PayPal) may refuse to play ball
For the really paranoid out there, it is possible to route a VPN connection through Tor, or an OpenVPN connection through an SSL or SSH tunnel (in order to hide its use). More details about these methods can be found here.
A final note regarding Tor is that it makes the anarchic and entirely unregulated Silk Road style marketplaces possible (such as Silk Road 2.0), as the online black market exists entirely within the Tor network (and therefore has no need for vulnerable exit nodes). Although supposedly set up on libertarian ideals, much of the actively on these marketplaces is highly illegal, so if you are curious then you will have to investigate further on your own.
in our opinion they are inferior to VPN.
Other services which may be of interest include JonDonym, http://www.bestvpn.com/blog/6507/lahana-service-aims-to-circumvent-censorship-in-turkey/, I2P and Psiphon. Interestingly, many such services can be combined with Tor and/or VPN for greater security.
cookies, how to clear them, and that most browsers now have aPrivate Browsing mode that not only prevents the browser from saving your internet history, but also blocks these cookies. It is therefore a good idea to always surf using Private Browsing, but this alone is not enough to stop you being tracked across the internet, as your browser leaves many other traces as it goes…

In Windows you can see what DNS information has been cached by typing ‘ipconfig /displaydns’ at the command prompt (cmd.exe)
- To clear the DNS cache in Windows,open the command prompt window and type: ipconfig /flushdns [enter]
- To clear the cache in OSX 10.4 and under, open Terminal and type: lookupd -flushcache
- To clear the cache in OSX 10.5 and above, open Terminal and type: dscacheutil -flushcache
Thanks to growing awareness of Flash cookies, including the so-called ‘zombie cookies’ (bits of persistent Flash code which respawn regular cookies when they are modified or deleted), and the fact that most modern browsers include Flash cookies as part of their regular cookie control features, the use of Flash cookies is declining (although they still represent a serious threat).
We have a detailed article on Flash cookies, the dangers they pose, and how to prevent them available here.
this article.
Interestingly, the recently released Privacy Badger browser plugin from the Electronic Frontier Foundation promises that it will add protection against fingerprinting, although how this will work we have no idea. Once it has been implemented and we have had a chance to test it out, we will update this section.
HTML web storage – built into HTML5 (the much vaunted replacement to Flash) is Web storage (also known as DOM (Document Object Model) storage). Even creepier and much more powerful than cookies, web storage is a way analogous to cookies of storing data in a web browser, but which is much more persistent, has a much greater storage capacity, and which cannot normally be monitored, read, or selectively removed from your web browser.
Web storage is enabled in all browsers by default, but in Firefox and Internet Explorer it can be turned off. Firefox users can also configure the https://addons.mozilla.org/en-US/firefox/addon/betterprivacy/addon to remove web storage automatically on a regular basis, or you can use the https://addons.mozilla.org/en-US/firefox/addon/clickclean/ addon, while Chrome users can use the Click&Clean extension or, alternatively, the versatilehttps://chrome.google.com/extensions/detail/odjhifogjcknibkahlpidmdajjpkkcfn extension (but this requires a high degree of configuring). Remember that using these addons will increase you browser fingerprint uniqueness. More details, including instructions on how to web storage off in Firefox and IE are available in our article here.
ETags – part of HTTP, the protocol for the World Wide Web, Etags are markers used by your browser to track resource changes at specific URL. By comparing these changes in these markers with a database, websites can build up a fingerprint which can be used to track you. They can also be used to respawn (Zombie style) HTTP and HTML5 cookies, and once set on one site, used by associate companies to also track you.
Unfortunately this kind of cache tracking is virtually undetectable, so reliable prevention is very hard. Clearing your cache between each website you visit should work, as should turning off your cache altogether. Unfortunately these methods are arduous, and will negatively impact your browsing experience. The Firefox add-on Secret Agent prevents tracking by ETags, but, again, will likely increase your browser fingerprint (or because of the way it works, maybe not). For more details see here.
History stealing – Now we start to get really scary. History stealing (also known as history snooping) exploits the way in which the Web is designed, allowing a website you visit to discover your past browsing history. Seeour article for a fuller explanation of how it works, but the bad news is, a) this information can be combined with social network profiling to uniquely identify you and, b) it is almost impossible to prevent.
The only good news here is that social network fingerprinting, while scarily effective, is not reliable, and if you mask your IP address with a VPN (or Tor) then you will be going a long way towards disassociating your real identity from your tracked web behavior.
AdBlock Plus (Firefox, Chrome, Opera, Android) – this fantastic and must-have extension blocks all manner of adverts, even Facebook ads and those embedded within YouTube videos (here in the UK it even blocks 4oD ads!). In addition to this, it warns you when visiting known malware hosting websites, and disables third party tracking cookies and scripts. Unlike NoScript (see below), AdBlock Plus is very easy to use while still remaining powerful. By default, AdBlock Plus allows ‘some not intrusive advertising’. This can be turned off (Add-ons -> Extensions -> AdBock Plus -> Filter preferences), or you can install AdBlock Edge for Firefox, a fork of AdBlock Plus that removes this ‘feature’
- Disconnect (Firefox, Chrome, Safari, IE) – replacing popular Ghostery as our favorite anti-tracking and anti-cookie extension thanks to its up-to-date database of tracking cookies, page load optimization, secure WiFi encryption and analytics tools, Disconnect blocks third party tracking cookies and gives you control of over all a website’s elements. It also prevents social networks such as Google, Facebook and Twitter from following you so they can collect data as you surf elsewhere on the internet
- HTTPS Everywhere (Firefox and Chrome) – another essential tool, HTTPS Everywhere was developed by the Electronic Frontier Foundation, and tries to ensure that you always connect to a website using a secure HTTPS connection, if one is available. This is fantastic, but do remember the reservations about how SSL is commonly implemented that we made earlier, and that it has almost certainly been cracked by the NSA
- https://addons.mozilla.org/en-US/firefox/addon/betterprivacy/ (Firefox) – as noted in the section on Flash cookies above, this extension blocks this new kind of cookie
- Honorable mention: NoScript (Firefox) – this is an extremely powerful tool that gives you unparalleled control over what scripts are run on your browser. However, many websites will not play game with NoScript, and it requires a fair bit of technical knowledge to configure and tweak it to work the way you want it to. It is easy to add exceptions to a whitelist, but even this requires some understanding of the risks that might be involved. Not for the casual user then, but for web savvy power-users, NoScript is difficult to beat. https://chrome.google.com/webstore/detail/scriptsafe/oiigbmnaadbkfbmpbfijlflahbdbdgdf for Chrome performs a similar job. Reader’s tip: ‘I would recommend adding that even if you don’t want to bother messing with white lists in Noscript, you should still install the extension and choose to allow all scripts globally. This still provides some needed protection without hindering your browsing experience.’ (Thanks twlph!)
Note that this list is not exhaustive of all the great privacy related browser extensions out there, and there are good articles about other extensions for Firefox and https://www.bestvpn.com/blog/9019/recommended-chrome-and-chromium-security-extensions/. We also have an article on how you make Firefox even more secure by changing setting in about:config.
Also, as noted above, you should be aware that using any browser plugin increases your browser uniqueness, which makes you more susceptible to being tracked by browser fingerprinting. Unfortunately there is little practical most of us can do about it (although the EFF promise to add Fingerprinting protection to Privacy Badger).


Google Transparency Report on the number of User Data Requests received, and the number (at least partially) acceded to.
There are however some search engines that do not collect user’s data. DuckDuckGo in particular has grabbed the headlines of late, with its popularity shooting through the roof following the NSA spying revelations (daily searches on DuckDuckGo jumped from the 2 million it had built up over the last four and a half years, to 3 million in just 8 days!).
An added benefit of using a search engine that does not track you is that it avoids the ‘filter bubble’. Most search engines use your past search terms (and things you ‘Like’ on social networks) to profile you, so they can return results they think will interest you. This can result in only receiving search returns that agree with your point of view, locking you into a ‘filter bubble’ where you do not get to see alternative viewpoints and opinions because they have been downgraded in your search results.
Not only does this deny you access to the rich texture and multiplicity of human input, but it can also be very dangerous as it can confirm prejudices and prevent you from seeing the ‘bigger picture’.
DuckDuckGo – the best known alternative search engine, and one we have examined in some detailhere, DuckDuckGo pledges not to track it users. Each search event is anonymous, and while it could in theory be tracked, there is no profile attached that can be accessed by infiltrators. DuckDuckGo says that it would comply with ordered legal requests, but as it doesn’t track users, ‘there is nothing useful to give them’. In use we have found DuckDuckGo to be very good, and through the use of ‘bangs’, it can also be made to search most other popular search engines anonymously too
- StartPage (formerly Ixquick)– searches many popular search engines simultaneously and anonymously, giving a star to results each time they are in the top ten of a search engine result. Ixquick promises not to store or share any personal information, or use any identifying cookies
- Gibiru – provides basic Google search engine results, but separates your query from your IP with the use of proxy servers. In addition to this, Gibiru deletes all records within seconds of performing a search, so ‘there is no profile data to sell, package or give away via partnership, request or subpoena’
- YaCy – the above search engines rely on trusting the search engine providers to maintain your anonymity. If this really worries you, then you might like to consider YaCy, a decentralized, distributed search engine built using P2P technology. This is a fantastic idea, and one that we really hope takes off, but for now it is more of an exciting curiosity than a fully-fledged and useful Google alternative.

To turn Search History off, click on the gear icon on the top right, and select ‘Settings’…

the weakness in the way in which SSL is commonly implemented.
However, all this is no good if the email service is simply handing over your information to an adversary (asGoogle and Microsoft have been doing with the NSA). While it seems that smaller email providers have not (yet) been affected, it is likely that as the NSA and other national government surveillance organizations extend their reach, this will change.
The answer to this problem lies in end-to-end email encryption, where the sender encrypts the email, and only the intended recipient can decrypt it. The biggest problem with using an encrypted email system is that you cannot impose it unilaterally – your contacts, both recipients and senders, also need to play ball for the whole thing to work, and while trying convincing your granny to use PGP encryption will likely just lead to bafflement, trying to convince your customers might make many of them very suspicious!
It should also be noted that email encryption does not encrypt everything. The email addresses of sender and recipient, date and time of sending, and the e-mail’s subject line are not encrypted; just the body and any attachments. As we briefly discussed earlier, metadata such as this can still be very damaging in the wrong hands.
Another point worth bearing in mind if you are worried about NSA spying is that, probably even more than encrypting other aspects of your internet use, encrypting your email is pretty much asking for the NSA to store your emails ready for decryption when they are able to do so.
Pretty Good Privacy (PGP, which was once open source and free, but is now the property of Symantic). The Free Software Foundation has taken up the open source OpenPGP banner however, and with major funding from the German government has released GNU Privacy Guard (also known as GnuPG or just GPG).

An overview of how the OpenPGP standard works
Following the OpenPGP standard and fully compatible with PGP, GnuPG is a free and open source alternative which is available for Windows, OSX and Linux. Although the basic program uses a simple command line interface, more sophisticated versions are available for Windows (Gpg4win) and Mac (GPGTools). Alternately,EnigMail adds GnuPG functionality to the Thunderbird and SeaMonkey email clients. We have written a full guide to setting up GnuPG in Windows using Gpg4win, available here.
https://play.google.com/store/apps/details?id=info.guardianproject.gpg&feature=related_apps#?t=W251bGwsMSwxLDEwOSwiaW5mby5ndWFyZGlhbnByb2plY3QuZ3BnIl0. from the Guardian Project is available from the Play Store., and although we have not tried them, mobile users wanting a more user-friendly experience may want to give K-9 Mail (a well-regarded email client with PGP support built-in) combined withhttps://code.google.com/p/android-privacy-guard/ (Android), or iPGMail (iOS) a try. A good guide for getting GPG working on Android is available http://geekyschmidt.com/2010/12/09/gpg-on-your-android-phone.
Hushmail was considered the go-to service for secure webmail, as it offered PGP encryption in a web based service. However, in 2007 a backdoor was used by the owners to capture emails of three accounts, which were then handed over to the Canadian Courts. As Hushmail CTO Brian Smith said in refreshingly honestblog post,
‘[Hushmail] is useful for avoiding general Carnivore-type government surveillance, and protecting your data from hackers, but definitely not suitable for protecting your data if you are engaging in illegal activity that could result in a Canadian court order.’
It should be noted that any web-based service can in theory be compelled to modify their system to capture users’ decryption keys (as Hushmail did), and Hushmail itself recommends using non web-based services such as GnuPG or PGP Desktop if stronger security is needed.
https://addons.mozilla.org/en-US/firefox/addon/encrypted-communication/we’ve written a guide about how to use it) which provides 256-bit AES end-to-end encryption. Once the extension is installed, just write your email, right-click anywhere in the text of the message and select ‘Encrypted Communication’ to encrypt it. You will be asked to enter a password, which the recipient will need to know (along with having the extension running on their Firefox) to decrypt the message. Of course, you should transmit this password to the recipient using a different communication method than email (in person is best, but encrypted VoIP or messaging should be fine – see below)!
Even more secure is Mailvelope, which provides full end-to-end OpenPGP encryption over web email services such as Gmail, Hotmail, Yahoo! and GMX using Firefox or Chrome. We have a full guide to using it availablehere.
Note that there are other extensions available which seem to offer similar functionality and which we often see recommended on the internet, but which should be avoided. Both https://chrome.google.com/webstore/detail/safegmail/lmjkmpdndmbieflefonjgnnfimmkbedf?utm_source=chrome-ntp-icon for Chrome and Enlocked(multiplatform) send your email to their servers for decryption, which means that it at least as vulnerable as mail sent to Hushmail (i.e. they do not offer end-to-end encryption). Furthermore, the SafeMail decryption page is not even SSL encrypted!
elsewhere, but it is worth briefly noting here that if it is just files you wish to protect, these can be encrypted before sending them by regular email.
It is also possible to encrypt stored emails by encrypting the email storage folder using a program such as TrueCrypt (discussed later). explains where Thunderbird stores emails on different platforms (for example).
metadata, and it is also totally pointless unless the people you are calling are equally paranoid.
as happened with Skype) or some other government origination, this security is next to meaningless.
So, as with email, what is needed is end-to-end encryption where an encrypted tunnel is created directly between the participants in a conversation, and no-one else.
Jitsi (Windows, OSX, Linux, Android (experimental)) – this free and open source software offers all the functionality of Skype, including voice calls, video conferencing, file transfer and Chat, but can encrypt it all with ZRTP. The first time you connect to someone it can take a minute or two to set up the encrypted connection (designated by a padlock), but is afterwards transparent. As a straight Skype replacement, Jitsi is difficult to beat
- RedPhone (Android) – this free and open source Android only app provides end-to-end encryption of voice calls. Unlike normal VoIP apps however, it lets you use your normal phone number and the normal system dialer, so operation is almost invisible, except that when you connect to someone else with RedPhone installed, you are given to option to encrypt the call
- Silent Circle – is a popular commercial suite of encrypted communications software comprised of Silent Phone (iOS, Android), Silent Text, (iOS, Android), Silent Eyes (Windows VoIP), https://www.bestvpn.com/blog/7919/lavabit-silent-circle-announce-plans-dark-mail/(iOS, Android, Outlook for Windows, Mac Mail). The service costs $10 per month, but the software itself is open source and has been audited by the American Civil Liberties Union to ensure it contains no ‘backdoors’. Reassuringly (in a way), the makers of Silent Circle recently closed their ‘Silent Mail’ service following the abrupt shutting down of Lavabit, in order to ‘prevent spying’.
- Addium (OSX) –is a free and open source messaging client for Mac that also lets you talk to friends on lots of different networks. Even better, Addium comes with OTR support built-in!
- TextSecure (Android, iOS) – sister app to Whisper System’s RedPhone, free and open source TextSecure replaces your Android’s default text app with one that encrypts texts to other TextSecure users, and encrypts all local messages so that if your phone is stolen they will remain secure. TextSecure has now been incorporated into alternative Android OS CynagenMod, expanding its userbase by around 10 million.
- Chatsecure (was Gibberbot) (Windows, OSX, Linux, iOS, Android) – developed by the Guardian Project, this app is available on all major platforms, supports chatting on a whole host of different IM services, and has OTR built-in. It is still a little buggy and no-frills, but has great potential.
Ditch the cell phone!
While we are on the subject of phones (sort of), we thought we should also mention that when you carry your phone, your every movement can be tracked. It’s not just things like GPS and Google Now (which works uncannily well at predicting what you want by storing just about every piece of data about you) on Smartphones – even the most modest cell phone can be easily tracked by the phone towersit uses to work. The only solution, if you really don’t want to be tracked, is to leave your phone at home (or buy one of these). Incidentally, the Google Now service only works effectively if Goggle History is turned on (see above).
reserve the right to investigate your files and hand them over to the authorities if they receive a court order.
To ensure that your files are secure, there are a number of basic approaches you can take (note that the options discussed below are far from the only ones available, as this is a highly competitive market space where many new and innovative solutions are appearing all the time)…
http://www.bestvpn.com/wp-admin/post.php?post=7096&action=edit&message=1#truecrypt. This has the advantage that you can carry on using your favorite Cloud storage service, no matter how inherently insecure it is, as you hold all the encryption keys to your files.
The downside compared to services such as SpiderOak and Wuala (see below), is that you don’t get access to your files on the go.
here.
If you are in the market for a good Dropbox alternative, you may like to check out BestVPN’s sister websiteBestBackups, for news and reviews of the best and the rest when it comes to cloud storage services.
Use an automatically encrypted cloud service
These services automatically encrypt files before uploading them to the Cloud (we have no truck with any service that encrypts files server-side, as these are always vulnerable to being decrypted by the service provider). Any changes to files or folders are synced with local decrypted versions before being secured and sent to the Cloud.
Both SpiderOak and Wuala have iOS and Android apps, so you can easily sync across all your computers and mobile devices. This convenience comes at a small security price, as both services briefly store your password on their servers to authenticate you and direct you to your files. Wuala also uses this password to encrypt and decrypt your files when using a mobile device, although this is somewhat compensated for by Wuala uploading different segments of your files to different servers, making it impossible for them to identify which data belongs to which user. In both cases the passwords are deleted once a session is finished.
- SpiderOak (2GB free, $10/m 100GB) – available for all major platforms, SpiderOak offers a ‘zero knowledge’, secure, automatically encrypted cloud service, which uses a combination of 2048 bit RSA and 256 bit AES to encrypt your files
- Wuala(5GB free, plans from €2/m 20GB to €160/m 2TB) – available for most major platforms and also offering 2048 bit RSA and 256 bit AESencryption (with SHA-256 hashes for integrity checks), Wuala’s service is very similar to that of SpiderOaks, but with a slightly different approach to security (see above).
Because of its high profile, we feel that Kim Dotcom’s Mega service deserves a special mention, particularly as it offers a very generous 50GB encrypted space for free. Mega uses your web browser to encrypt files before uploading and decrypt them after downloading, which is great for convenience (and an Android app is available, with an iOS one on the way), but is not as secure as the other methods outlined here.
Our feeling therefore, is that while it is worth paying attention to how Mega deals with its security issues, it is probably best avoided for the time being. It is also worth pointing out that Kim Dotcom’s involvement ensures the service receives the highest possible level of scrutiny from security, law enforcement and copyright enforcement bodies the world over.
BitTorrent Sync service is now in public beta phase (i.e. it is available to the public, but is still considered experimental). Designed more or less as a Dropbox replacement, BitTorrent Sync synchronizes files and folders across devices, but does so without storing them in ‘the Cloud’.
You chose a folder that you want to share, and BitTorrent Sync gives you a secret for it. You can then link that folder to a folder on another device (with BitTorrent installed on it) using the secret. Any number of additional folders can be added in a similar fashion, and all files are transferred using a securely encrypted (256-bit AES) P2P protocol.
BitTorrent Sync is free, easy to use, and is currently available for Windows, OSX , Linux and Android (with an iOS app in private alpha stage). A limitation of the system is that as it is not a cloud service, it cannot be used as an extra drive by portable devices with limited storage, but on the plus side you are using your own storage, and so are not tied to Cloud providers’ data limits (or charges).
pulled the plug on the popular full-disk encryption program. Conspiracy theories abound, and while some developers seek to fork the software, Phase II of the audit goes ahead. For more details on the story see here and here. Until the audit is complete, we strongly suggest avoiding TrueCrypt, and migrating TrueCrypt containers to other programs, such as to https://diskcryptor.net/wiki/Main_Page for Windows users, or https://code.google.com/p/cryptsetup/ and bwalex/tc-play (a free TrueCrypt Implementation based on dm-crypt) for Linux users.
While other solutions are of course available, the king of local encryption is undoubtedly the powerful free/donationware, open source program TrueCrypt(available on Windows, OSX and Linux).

TrueCrypt can be used to create encrypted volumes on your computer, to encrypt entire disks, to create hidden volumes, and even to create an entire hidden operating system (using 256-bit AES, or any of a number of user specified encryption schemes). What makes Truecrypt so powerful and easy to use is on-the-fly encryption, which allows you to work with files as you would on normal, unencrypted files, without the hassle of continually encrypting and decrypting them. Once a volume is mounted (using a password), then operation is transparent, with TrueCrypt keeping temporary files in RAM. and generally cleaning up after itself once a session is finished.
For ultimate security, you can encrypt the drive your operating system is installed on, which will ensure that all the little system files and other bits of junk that OS’s tend to create remain secure. Of course, if you forget your password then you won’t be able to boot into your system! TrueCrypt will also even let you create a container with hidden Operating System in it (see below)!
TrueCrypt allows you to create hidden volumes, which provides’ plausible deniability’ as it is impossible to prove that a second volume exists. This is great in situations where guilt must be proven, but also means that if this is not the case (e.g. in repressive countries where innocence must be proven), it is impossible to prove a hidden volume does not exist either (which may result in imprisonment or torture based on the assumption that it does exist!). We have written a post on this subject examining the issue in more depth.
crowdfunded project to properly audit TrueCrypt’s code has now been completed, and the results are somewhat worrying. ‘iSEC found no evidence of backdoors or otherwise intentionally malicious code in the assessed areas,’ but some very sloppy code was discovered that ‘did not meet expected standards for secure code.’
This is hardly encouraging given the massive resources that the NSA deploys to uncover just such weaknesses, and leads us to worry that these flaws have already been discovered by them. Nevertheless, TrueCrypt remains the best encryption method available, and was enough to see off the police in the http://www.reuters.com/article/2013/08/30/us-usa-security-snowden-nytimes-idUSBRE97T0RC20130830.
Cyrptonite brings TrueCrypt and http://www.arg0.net/encfs to Android, including allowing users to access TrueCrypt containers (if you experience problems, a command line version of TrueCrypt is included with the app). EDS Lite is another good option that does more or less the same.
Unfortunately there is no TrueCrypt compatible app or alternative available for iOS devices that we are aware of.
Part 1 Part 2.
Alternatives to Truecrypt
If the the auditing results for TrueCrypt or the implications of ‘plausible deniability’ worry you, there are a couple of other highly regarded encryption programs available:
- eCryptfs (Enterprise Cryptographic Filesystem) (Linux) – looks like TrueCrypt (which uses encrypted containers) as it creates a folder that transparently decrypts/encrypts all files placed into out of it seamlessly and on the fly, but differs as each file is encrypted separately, and if you unmount the folder you end up a number of singly encrypted files (i.e. it provides per-file encryption)
- Tomb (Linux) – a FOSS script that creates encrypted folders using LUKS AES/SHA-256 encryption
Use antivirus, anti-malware and firewall software
BestAntivirus.com. If you would like to choose an antivirus package that best fits your needs, please take the time to check it out! Now, back to the guide…

It almost goes without saying, but as this is an ‘ultimate guide’ we’ll say it anyway… always use anti-virus software and make sure that it is up-to-date!
Not only can viruses really screw up your system, but they can let hackers enter it, giving them access to all your (unencrypted) files and emails etc., webcam, passwords stored in Firefox (if no master password is set), and much more. Keyloggers are particularly dangerous as they can be used to access bank details and track pretty much everything you do on your computer.
It is also worth remembering that not just criminal hackers use viruses! The Syrian government, for example, launched a virus campaign known as Blackshade, aimed at ferreting out and spying on political dissidents.
Although most people are aware they should be using anti-virus software on their desktop computers, many neglect their mobile devices. While there are less viruses targeting mobile devices at present, smart phones and tablets are sophisticated and powerful computers, and as such are vulnerable to attack by viruses, and should therefore be protected.
Mac users are famously bad for not installing ant-virus software, citing the ‘fact’ that OSX’s Unix architecture makes virus attacks difficult (this is hotly contested by the way), the fact that most hackers concentrate on Windows because most computers use Windows (true), and the anecdotal evidence of many Mac users who have gone for years without using anti-virus software yet never experienced any problems. However as events last year demonstrated, Macs are not immune to viruses, and anyone serious about their security should always use good anti-virus software.
consensus is that free antivirus software is as good at preventing viruses as paid-for alternatives, but paid-for software provides better support and more comprehensive ’suites’ of software that are designed to protect your computer from a range of threats (combining antivirus, anti-phishing, anti-malware and firewall functions for example). Similar levels of protection are available for free, but require the use of various different programs. Also, most free software is for personal use only, and businesses are usually required to pay for a license.
Some good anti-virus software:
- Windows – the most popular free antivirus programs for Windows are Avast! Free Antivirus andAVG AntriVirus Free Edition, although plenty of others are also available. A good review of commercial options can be found here
- OSX – Avast! Free Antivirus for Mac and ClamXav are well regarded, although other free good optionsare available. In fact, the free software is better regarded than paid-for options, so we just recommend using them
- Android – again, there are a number of options, both free and paid for. We’ve used Avast! for ages now and find it works well, is free, and includes a firewall
- iOS – Apple is still somewhat in denial about the fact iOS is as vulnerable as any other platform to virus attack, but VirusBarrier is now available from the app store
- Linux –the usual suspects: Avast!, Kaspersky and AVG Free are all available for Linux, work very well, and are free.
Comodo Firewall Free and ZoneAlarm Free Firewall 2013, which are good free options
- OSX – versions 10.5 and up have a basic firewall built-in, which like that in Windows only monitors incoming traffic. If you want to monitor outgoing traffic, Little Snitch ($25) is a great program
- Android – as noted above, the free Avast! For Android includes a firewall
- iOS – the only iOS firewall we are aware of is Firewall iP, which requires a jailbroken device to run
- Linux – there are many firewall programs and dedicated firewall distros available, but for a simple and straight forward Linux firewall you might want to give Smoothwall a try.
Unfortunately, despite great strides made in the right direction, Linux remains less user friendly than either Windows or OSX, and less computer literate users may struggle with it. If you are serious about privacy however, Linux really is the way forward, and one of the best things about it is that you can run the entire OS from a Live CD, without the need to install it. This not only makes it easy to try out different Linux distros, but also adds an extra layer of security when you access the internet.
Ubuntu is very popular due to the fact that it is one of the easiest Linux distros to use, and thanks to this popularity there is a great deal of assistance available for it from an enthusiastic Ubuntu community. It therefore makes a good starting point for those interested in a using a much more secure Operating System.
More experienced users however might want to take a look at Tails, a Linux distro built from the ground up to preserve privacy and anonymity, and which forces all connection to go through Tor.
Puppy can help, as does installing the VM on a separate hard drive to your main OS.
Popular VM software includes the free VirtualBox and VMWare Player, and the premium ($273.90) enterprise level VMware Workstation. As noted above, TrueCrypt lets you encrypt an OS, or even hide one.
VirtualBox Virual Machine, and ensures that DNS leaks are not possible, and that ‘not even malware with root privileges can find out the user’s real IP’.

It consists of two parts, the first of which acts as a Tor gateway (known as Whonix Gateway), while the second (known as a Whonix Workstation) is on a completely isolated network which routes all its connections through the Tor gateway. This isolation of the workstation away from the internet connection (and all isolated from the host OS inside a VM), makes Whonix highly secure.
insecure piece of software (see also Flash Cookies), but despite the gains made by HTML5, it remains an important part of most people’s internet user experience. It is therefore a good idea to check its settings, and turn off most of them off (paying particular attention to the Camera and Mic settings!).
Many security related browser plugins disable Flash by default, which a good thing, but does not help when you actually want view the Flash content. Be careful however to only allow Flash on trusted websites. The Flash Player Settings Manager has moved from being online to being accessed locally, and the easiest way to open it is to right-click on some Flash content (e.g. a YouTube video) and select ‘Global Settings…’.

www.bestvpn.com to its IP address of 216.172.189.144, the Domain Name System (DNS) is used.
By default this translation process is performed on your ISP’s DNS servers, which ensures your ISP has a record of all websites you visit. Even when using a VPN service (highly recommended), possible DNS leakage may result in your ISP handling this DNS translation instead of your VPN provider (as should happen).
Fortunately, there are a number of free and secure public DNS servers, including OpenDNS and Comodo Secure DNS, although we prefer the non-profit, decentralized, open, uncensored and democratic OpenNic(which we discuss here). We recommend changing your system settings to use one these instead of your ISP’s servers, and have instructions of how to do this in Windows 7 (along with a guide on how to detect and block DNS leaks when using a VPN) available here.
DNS was not built with security in mind and it is vulnerable to a number of attacks, the most important of which is a ‘man-in-the-middle’ attack known as DNS spoofing (or DNS cache poisoning), where the attacker intercepts and redirects a DNS request. This could, for example, be used to redirect a legitimate request for a banking service to a ‘spoof’ website designed to collect account details and passwords for unsuspecting victims.
This has prompted the chaps at OpenDNS to develop http://www.opendns.com/technology/dnscrypt/, a lightweight program that encrypts ‘all DNS traffic between the user and OpenDNS, preventing any spying, spoofing or man-in-the-middle attacks’. Using Curve25519 elliptical-curve cryptography, DNSCrypt is available for Windows, OSX and Linux, and although in ‘preview release’ stage, is considered stable. The only issue is that OpenDNS is run by a private company (which is why we prefer OpenNic), but it is currently the only program of its kind available.
set a master password to prevent just anyone peeking at your passwords in Firefox’s options dialogue. In addition to this, it is probably a god idea to back up your Firefox passwords every now and again
- KeePass(multi-platform)– this popular free and open source password manager will generate complex passwords for you and store them behind AES or Twofish encryption. It is a shame that KeePass doesn’t integrate with your browser, but it is possible to import saved Firefox passwords into it. KeePass itself is Windows only, but KeepassX is an open source clone for OSX and Linux, as arehttps://itunes.apple.com/us/app/ikeepass/id299697688 for iOS and Keepass2Android for Android
- Keep private conversations private – it is all too common for people to discuss intimate details of a planned dinner date, or conversely to have personal rows using public channels. Remember that things like Message (Facebook) and DM (Twitter) exist, and use them. It won’t hide your conversations from advertisers, the law, or the NSA, but it will at least keep potentially embarrassing interactions away from friends and loved ones (who probably really don’t want to hear certain things anyway!)
- Use aliases – despite what the likes of Facebook try to insist upon, there is nothing stopping you from using a false name. In fact, in this world where employers almost routinely check their staff’s (and potential staff’s) Facebook pages, using at least two aliases – a sensible one with your real name which is designed to make you look good to employers, and another where friends can post wildly drunken pictures of you, is almost a must. Remember that it is not just names you can lie about; you can also happily fib away about your date of birth, interests, gender, where you live, or anything else that will put advertisers and other trackers off the scent. On a more serious note, bloggers living under repressive regimes should always use aliases (together with IP cloaking measures such as VPN) when making posts that may threaten their life or liberty
- Keep checking your privacy settings – although Facebook is notorious for continually changing the way its privacy settings work, and for making their privacy policies as opaque as possible, it is worth regularly checking the privacy settings on all social networks to make sure they are as tight as possible (for example by ensuring that posts and photos are only shared with Friends, not Friends of Friends or ‘Public’). A good idea in Facebook is to ensure that ‘Review posts friends tag you in before they appear on your time line’ (under Privacy Settings -> Timeline and Tagging) is set to ‘On’, to help limit the damage ‘friends’ can do to your profile .
- Use Diaspora instead – Diaspora is a nonprofit, open source, user-owned, distributed social network that is based upon the free Diaspora software It is constructed of a network of nodes (called pods)hosted by volunteer individuals and institutions, and which act as personal web servers. Users of the network can host a pod on their own server or create an account on any existing pod of their choice, and from that pod can interact with other users on all other pods. As of March 2014 there are more than 1 million Diaspora accounts, and although it is a still very much a work in progress (and you will need to convince your friends to join on the network – always the biggest hurdle when moving away from Facebook), Diaspora is the most complete open source Facebook alternative available.
While other countries’ governments’ seem desperate to increase their own control over their citizen’s data, nothing (including China’s attempts at internet surveillance) matches the scale, sophistication or reach of PRISM.
It is therefore a very good idea, if such things worry you (as they should), to avoid all dealings with US companies where you are concerned about your privacy. To suggest that every US company may be complicit in handing every user’s personal information over to a secretive and largely unaccountable spying organization might sound the stuff of paranoid science fiction fantasy, but as recent events have proved, is terrifyingly close to the truth…
Note also that due to provisions in both the Patriot Act and the Foreign Intelligence Surveillance Act (FISA), US companies must https://www.bestvpn.com/blog/9620/us-forces-microsoft-to-hand-over-emails-stored-in-ireland/ even if that user is a non-US citizen, and the data has never been stored in the US.
In addition to this, the UK’s GHCQ is in bed with the NSA and carries out some particularly https://www.bestvpn.com/blog/8893/ghcq-grabs-millions-of-often-explicit-yahoo-webcam-images/spying projects of its own (‘They [GCHQ] are worse than the US’, Edward Snowden). Indeed, all members of the English speaking ‘Five Eyes‘ spying alliance (US,UK, Canada, Australia and New Zealand) share information between their security organizations and use each other to spy on their own citizens (to bypass national laws prohibiting this), and so companies based in these countries should also be similarity avoided.
Google Now is an excellent case in point. An ‘intelligent personal assistant’, this software’s ability to anticipate what information you require is uncanny. It can, for example remind you that you need to leave the office to catch the bus ‘now’ if you want to get home at your usual time, as well as providing navigation to the nearest bus-stop, and alternative timetables should you miss it. Google’s new, and possibly game-changing Google Glass system makes heavy use of Google Now technology, which relies on storing and curating large amounts of information about your habits, likes, dislikes, browsing history, where you like to drink, and much more.
In other words, some of the most exciting and interesting developments in human-computer interaction rely on a full-scale invasion of our privacy, and to box yourself in with encryption and other privacy protection methods is to reject the possibilities afforded by these new technologies.
We mainly pose the question ‘is privacy worth it’ as food for thought. Privacy comes with a cost, and it is worth thinking about what compromises you are willing to make, and how far you will go, to protect it. In our view privacy IS vitally important, as everyone has a right not to have almost every aspect of their lives recorded, examined and then judged or exploited (depending on who is doing the recording), but it has to be recognized that maintaining privacy is not easy (and can never be completely guaranteed) in the modern world.
Of course, what most of us probably want is the ability to share what we want with our friends and with services that improve our lives, without worrying this information is being shared, dissected and used to profile us for dubious ends. While this is not likely to happen soon, if more people make even fairly basic efforts to improve their security, it would make both government agencies’ and advertisers’ jobs much more difficult, to the point that it could even force a change of approach.
https://opentrackers.org/educateyourself/.

