I use TAILS on an old laptop when I need to be extra secure.
-
ATTENTION New Members: Please take a few moments to introduce yourself, show your commitment to harm reduction, and chat with the community in the "New Member Introduction" subforum. This will help unlock access to additional forum features and privileges.
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
How to not get fucked over by hackers or extortionists for the paranoid and inept at IT.
- Thread starter janoshik
- Start date
Artifex
Member
This thread definitely sticky !
Great information for everybody !
Great information for everybody !
And others can contribute to it. Yes for a sticky!
Cookieman
Member
Great write up and good info..So, I have a really stupid question. I haven't fooled with my proton account or jaxx wallet in quite some time. I just noticed that they are both completely gone from my phone. They aren't listed in apps either, and I didn't delete them. Have I been hacked? I had less than 20 bucks in the wallet. I just find it odd that just those 2 have vanished. Please pardon my ignorance
hfo369
New Member
This is vital information in these crazy times. Thank you for posting this
Apps can be removed remotely whenever the apps are removed totally from the app store. As for a hacker to remotely remove apps they would need access to the device remotely. Only way to do that is by remotely exploiting vulnerabilities in Android or iOS as the case may be and to be able to access your particular device.Great write up and good info..So, I have a really stupid question. I haven't fooled with my proton account or jaxx wallet in quite some time. I just noticed that they are both completely gone from my phone. They aren't listed in apps either, and I didn't delete them. Have I been hacked? I had less than 20 bucks in the wallet. I just find it odd that just those 2 have vanished. Please pardon my ignorance
janoshik
Subscriber
Just trying to underline the fact that links can lead somewhere you wouldn't expect, despite the way they lookGood write up. Glad you said it, 'cause Diane is a bitch, she's also a whore if you ask me.
Your website is a den of evil?
Are you trying to tell us something, Jano?

It's always better to demonstrate something - people are more likely to remember that than just a wall of text.
Hello my friend, this was aimed mostly for the customer part of the business who don't have to worry about that, but I'm sure your input will turn valuable for some, thank you.Tutanota isnt safe for business. Well encryption wise it is, but they will shut your email down easily. I know because my email has been closed. I advise all sources who use tutanota to switch over to proton asap. My tutanota email has been shutdown. I thought I was hacked for a minute, but i tried to email myself from a different email and i received a message "juicepal@tutanota.com does not exist"
I think the most probable reason is that is caused by an update or by "free up some space on your phone" kind of program removing them because you had not used them for a while.Great write up and good info..So, I have a really stupid question. I haven't fooled with my proton account or jaxx wallet in quite some time. I just noticed that they are both completely gone from my phone. They aren't listed in apps either, and I didn't delete them. Have I been hacked? I had less than 20 bucks in the wallet. I just find it odd that just those 2 have vanished. Please pardon my ignorance
If you remember the credentials you can try logging in again and checking things out.
ChatSecure.org (IOS) or Conversations.Im (Android)It's still better than proton encryption alone. Can you elaborate further on the subject of PGP vs Jabber vs OTR. I've always been of the understanding that you would using PGP with emails and OTR with instant messaging.
Ugh, wrong place but I have to do it... @balco , shut the fuck up.
Necessary Evil
Well-known Member
Great read, thanks for sharing.
Thoughts on Wickr as a means of communication?
Thoughts on Wickr as a means of communication?
janoshik
Subscriber
I use it for regular conversations, that are not too sensitive, however, I have not researched it too much.Great read, thanks for sharing.
Thoughts on Wickr as a means of communication?
It's not too likely it would get hacked, but in case you are arrested, your phone will be the first thing that's checked out and usually people stay logged in their messaging apps, so I consider it a security risk.
Last edited:
T-Bagger
Elite
So you don’t believe that once a Wickr message is burned, it’s gone for good?I use it for regular conversations, that are not too sensitive, however, I have not researched it too much.
It's not too likely it would get hacked, but in case you are arrested, your phone will be the first thing that's checked out and usually people stay logged in their messaging apps, so I consider it a security risk.
Exactly. Some people get upset with me because i dont open attachments I will not open attachments under any circumstances. I dont care who you are. It means nothing because a trusted individual could have been hacked and the hacker could be emailing the source(pretending to be someone else) with the infected file to gain access to his email.
You don’t even need to be a hacker to write from any email you want.
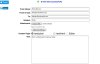
But it’s pretty easy not to fall for it,just need to be a bit suspicious. And these emails usually fall to spam folder on normal mail providers.
Last edited:
janoshik
Subscriber
It very well might be, but what happens if somebody gets his hands on your phone before it gets burned?So you don’t believe that once a Wickr message is burned, it’s gone for good?
T-Bagger
Elite
Always set messages to burn shortly after sent and important stuff should always be near instant.It very well might be, but what happens if somebody gets his hands on your phone before it gets burned?
janoshik
Subscriber
I agree with you, however I am skeptical about how many people would actually follow that. It gets real hard to keep track of stuff if it gets deleted that fast.Always set messages to burn shortly after sent and important stuff should always be near instant.
T-Bagger
Elite
True, and with the whole notification of screen shots, people get even more nervous.I agree with you, however I am skeptical about how many people would actually follow that. It gets real hard to keep track of stuff if it gets deleted that fast.
Wikr is also US based and not open source, so there is a lot of speculation as to how “secure” it truly is. One of the best options for encrypted communication would be ChatSecure/Conversations. Most of the others are not open source, and many of the “top rated secure messengers” require a phone number to sign up with (ironic huh?). The worst of all but actually rated “the most secure” is WhatsApp. Facebook owns WhatsApp, which is probably enough of a reason to stay the hell away from it at all costs. @neccesary evilI use it for regular conversations, that are not too sensitive, however, I have not researched it too much.
It's not too likely it would get hacked, but in case you are arrested, your phone will be the first thing that's checked out and usually people stay logged in their messaging apps, so I consider it a security risk.
+1You don’t even need to be a hacker to write from any email you want.
View attachment 119054
View attachment 119053
But it’s pretty easy not to fall for it,just need to be a bit suspicious. And these emails usually fall to spam folder on normal mail providers.
When an email is actually coming from a different domain than the real email, most email providers will place such email to spam folder. This is one trick spammers use as well. Good to always check the full mail headers to verify whether an email is legitimate or not.
To check URL's in links in an email just hover mouse pointer over over it, or right click the link and copy link location then paste into notepad to view the link. But as best practice do not click the links unless you absolutely trust the sender and the email checks out as legitimate.
T-Bagger
Elite
This hacker not only comes up with spoof emails, he takes over people’s emails to rip them off.
I've always wondered how sources can send using a tracked service without being captured on camera at the post office, mailbox shop etc surely it's the single biggest hole in their opsec.
Similar threads
- Sticky
MESO-Rx Sponsor
Avexshop.to - official distributor of Avex Pharma brand.
- Replies
- 12
- Views
- 1K
- Replies
- 52
- Views
- 2K
- Replies
- 10
- Views
- 408
- Replies
- 490
- Views
- 52K
Sponsors
Latest posts
-
10-20mg cialis is more effective than any expensive preworkout/pump product
- Latest: nightprowler7
-
-
-
